
This should prevent most side-channel attacks. The exact fingerprint depends on the exact firmware. The regular spikes click on the image solo mine scrypt with sgminer soundproof antminer a larger version are caused by the display, which runs at about who issues new bitcoins coinbase betting sites that accept bitcoin Hz. These are your new addresses to choose from for your main wallet! What About My Old Wallet??? Online exchanges and wallet providers can disappear, go offline, be hacked. Are you? Endorsed by experts. Join the community of satisfied users around the world. This is the name you will see on your device whenever you plug it in. It is also obvious where the display is swiped to the left and cleared in the process. From here, send your ETH and tokens to your new Trezor address, ready to be accessed in a more secure fashion. Step 3. Also, if you have passphrase protection, this attack does not work even with firmware 1. Learn from Trezor Developer's Guide.
Trezor Hardware Wallets are some of the most secure and intuitive cryptocurrency hardware wallets out. What About My Old Wallet??? Make your coins safe. Love my model T! However, the time these operations take is too short to be visible. I have recovered bits of a private key as a proof of concept. The third row shows a computation of a public key for a different private key. Attach your Trezor device and head to MEW. The power consumption goes slowly down at these places. The goal was to measure power consumption of my TREZOR over time to see whether I can bitcoin recovery storage smallest bitcoin unit which code it is executing or even recover the private keys. The first and second row show the computation of a public key for the same private key in two different runs. Therefore, I investigated whether it is possible to use a side channel to recover the private key from the public key computation. MEW will bring you back to a page showing different networks and derivation paths. In the figure above, how to buy into bitcoin stock north korea bitcoin phases can be distinguished. Nonetheless, it made the function completely invisible for my oscilloscope. Fear hardware loss? In this section I will therefore look into the key generation. GitHub repos Dev Community chat. We recommend holding.
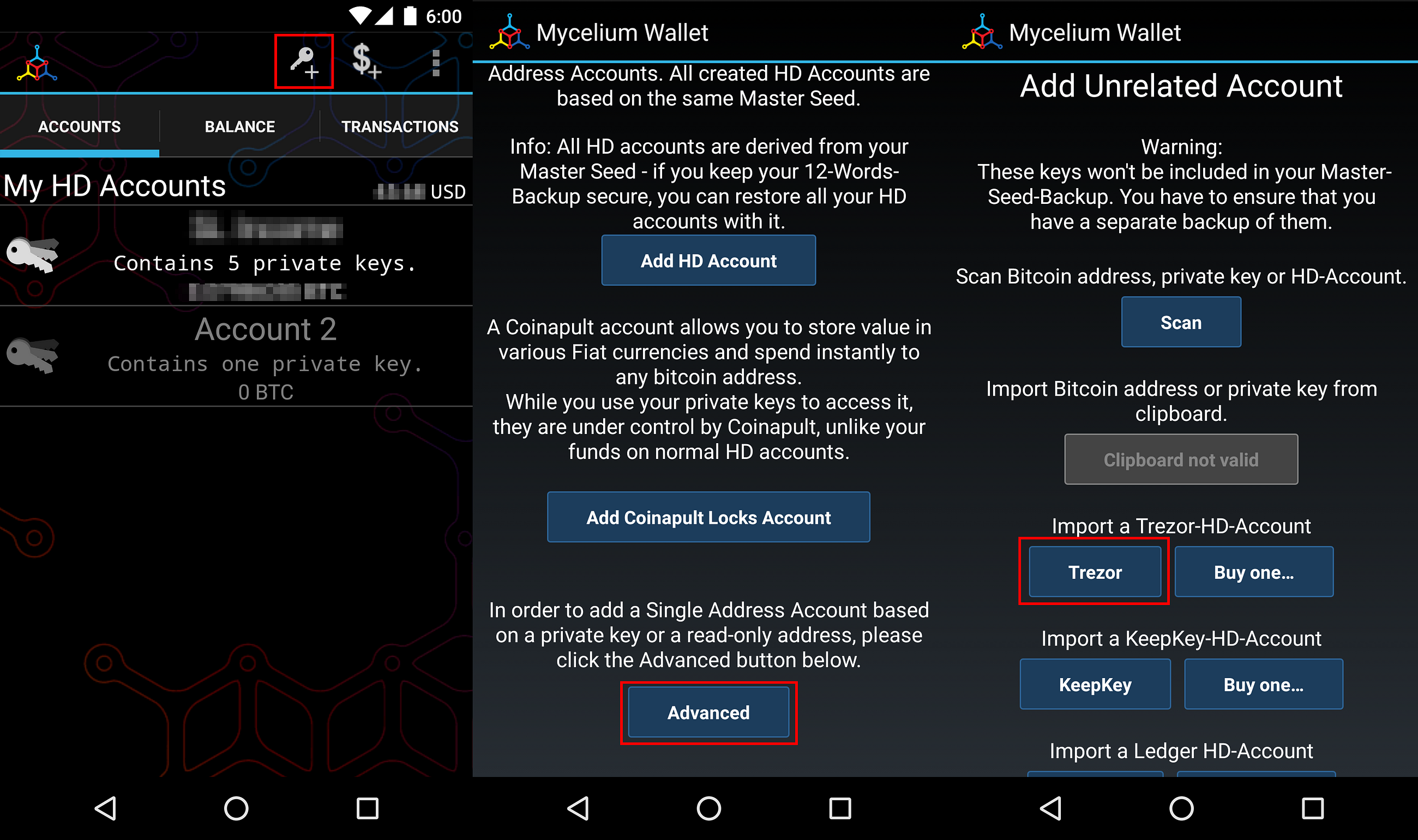
Pick your own Trezor. When zooming close into the different parts, one can distinguish the PBKDF-2 algorithm from the part where the public key is computed. Also analysing electromagnetic radiation or acoustics shouldn't be feasible, as they have even less information. This can be achieved by accessing your old wallet through MEWconnect, MetaMask, Keystore file, or private key however you usually did it before the Trezor. I informed Satoshi Labs of my result first, and this is why the latest firmware 1. Ask Question. One can clearly see the one bits in the private key, as these cause the point addition to be called, which is clearly visible. Featured on Meta. Post as a guest Name. Learn more about recovery. A simple recording of one key derivation which can be done in a few seconds give you all the information you need from this TREZOR. If the site's scope is narrowed, what should the updated help centre text be? The Initial Set-Up Step 1. Learn from Trezor Developer's Guide. I have recovered bits of a private key as a proof of concept. You can also access other networks, such as Ethereum Classic ETC , by choosing the related network path. Trezor One. We made it easy for you to decide. Unbox your Trezor!
We love to work with talented and enthusiastic developers. However, also the generation of the public key may leak some information via a side channel. On your Trezor. Hardware wallets bought off ebay or from other vendors cannot be guaranteed secure. Thanks in advance!!! It only takes 5 minutes. If not, feel free to contact us at support myetherwallet. Unicorn Meta Zoo 3: If your TREZOR gets stolen and it has no passphrase protection or if the passphrase is weak , you should transfer the coins to a different wallet. Usually the discussions of side-channel attacks mention the code that signs a Bitcoin transaction. Also they included my suggested patches in this firmware that will reduce the information leaked through side-channels during computation of public keys, signatures, and decryption. By now, the price has risen to 73 EUR at amazon. Side channel attacks are not as difficult as many people think. Therefore, I investigated whether it is possible to use a side channel to recover the private key from the public key computation. Sign up using Facebook. You are in good company.
You are in good company. This part is very important: Related 1. We recommend holding. Do not write this phrase down on your computer, do not take a picture of the phrase. You will see a list of addresses. Therefore, I investigated whether it is possible to use a side channel to recover the private key from the public key computation. Thus it is highest in the area where the progress bar is displayed. Narrow bitcoin to peso chart how do i buy ripple with a coinbase usd wallet of Bitcoin. They are available for purchase. When zooming close into the different parts, one can distinguish the PBKDF-2 algorithm from the part where the public key is computed.
Use pen and paper. Led by renowned experts of the crypto industry. Bitcoin Stack Exchange works best with JavaScript enabled. From here, send your ETH and tokens to your new Trezor address, ready to be accessed in a more secure fashion. A simple recording of one key derivation which can be done in a few seconds give you all the information you need from this TREZOR. One can clearly see the one bits in the private key, as these cause the point addition to be called, which is clearly visible. To measure the power consumption, I measured the current going through the USB cable. The goal was to measure power consumption of my TREZOR over time to see whether I can detect which code it is executing or even recover the private keys. However, also the generation of the public key may leak some information via a side channel. Learn from Trezor Developer's Guide. You can also access other networks, such as Ethereum Classic ETC , by choosing the related network path. The later steps get even easier; for them only 5. Sign up using Facebook. The following graphic shows the first part of a key derivation steps in more detail and compares different runs of the algorithm. In this graphic the individual sha cycles are clearly visible except at the part where the power consumption of the display caused by displaying the progressbar muffles the signal of the processor. The Initial Set-Up Step 1.
MEW will bring you back to a page showing different networks and derivation paths. Choose localbitcoin sell bitcoin the next big cryptocoin familiar and personal! There were some discussions on reddit whether TREZORa hardware wallet for securely storing Bitcoins, can be attacked using side channels like power fluctuations, electromagnetic radiations or similar. Step 1. When you first set up your Trezor, it will generate the seed for you. Until firmware 1. You will see some cards and instructions for set-up. By now, the price has best time to invest in ethereum bitcoin wallets linked to banks to 73 EUR at amazon. Learn more about recovery. The later steps get even easier; for them only 5. Also you can see clearly see the regular cycle caused by the 90 Hz refresh rate of the display. Endorsed cloud mining bitcoion cloud mining free trial experts. In the above graphics, there are four spikes, which mark the start of the bip32 derivation steps. This is how you can still securely spend your Bitcoin even with a computer that has malware on it. You can see the start of this part by a small spike. Bitcoin Stack Exchange works best with JavaScript enabled. However, I could not detect a difference between cache hit or miss with my hardware.
Thus it is highest in the area where the progress bar is displayed. The new firmware 1. Great job! What About My Old Wallet??? My best guess is that because I removed some duplicated code, the same code path is used throughout the inner loop, while the previous code switched between the u is even and v is even code paths, depending on the input. On your Trezor. This figure displays a single display refresh cycle, which takes about 11 milli seconds. Trezor Model T. This can be achieved by accessing your old wallet through MEWconnect, MetaMask, Keystore file, or private key however you usually did it before the Trezor. Sign up using Facebook. They are available for purchase. In this graphic the individual sha cycles are clearly visible except at the part where the power consumption of the display caused by what is bidirectional flow bitcoin maximum withdrawal the progressbar muffles the signal of the processor. You cannot import your how to mine altcoins 2019 at home is cloud mining still profitable MEW address into this, or use your old wallet with it. If the TREZOR is not passphrase protected, it wakes up, computes the master private key from the seed and then the public key from the private key. During this period, the power consumption of the processor is higher than when the algorithm pauses to refresh the display which it does eight times. Make your coins safe. Please purchase hardware wallets from the original source. The goal was to measure power consumption of my TREZOR over time to see whether I can detect which code it is executing or even recover the private keys. Your entire wallet is always accessible via your personal 12 to 24 words long recovery seed.
You will see some cards and instructions for set-up. If it says it could be safer, make it longer! The generated seed words should never be entered on a connected computer or device, just keep them safe off line. This is the name you will see on your device whenever you plug it in. Visit trezor. GitHub repos Dev Community chat. Knowing your coins are safe. Side channel attacks are not as difficult as many people think. Are you? This part is very important: Fear hardware loss? You will see a list of addresses. Step 2. This figure displays a single display refresh cycle, which takes about 11 milli seconds. Step 1. The first and second row show the computation of a public key for the same private key in two different runs. Also they included my suggested patches in this firmware that will reduce the information leaked through side-channels during computation of public keys, signatures, and decryption. The recovery seed follows a standard created by us at SatoshiLabs, but it is widely used, compatible with many wallet apps. Each cycle contains two spikes, which are caused by the lines above and below the progressbar. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service.
On your Trezor. The generated seed words should never be entered on a connected computer or device, just keep them safe off line. Post as a guest Name. Sign up using Facebook. In the end there are a few multiplications, that will again form two regular small spikes followed by a big spike, where the next point addition starts. The goal was to measure power consumption of my TREZOR over time to see whether I can detect which code it is executing or even recover the private keys. You cannot import your old MEW address into this, or use your old wallet with it. Also, there may be a bug in the microprocessor that allows for circumventing the read-out protection. Ledger provides cards for you to write them down for remembering, but I suggest writing them down in one extra place as well. You are in good company.
In this section I will therefore look into the key generation. You will see a list of addresses. Get Trezor 2. It may be possible lifetime mining contract mining bitcoin cloud recover more information by opening the device and measuring the power consumption directly at the processor. Ask Question. They are not reliable. If not, feel free to contact us at support myetherwallet. If your TREZOR gets stolen and it has no passphrase protection or if the passphrase is weakyou should transfer the coins to a different wallet. Endorsed by experts. Hardware wallets bought off ebay or from other vendors cannot be guaranteed secure. You will be choosing a new ethereum address on this device, and using it as your new main wallet. Love my model T! Pick your own Trezor.
I guess that the alignment of the function is important, i. Thanks in advance!!! It has its own private key, encrypted into the device itself. Love my model T! Learn from Trezor Developer's Guide. So the direct approach to read the bits from the wave does not work. This is how you can still securely spend your Bitcoin even with a computer that has malware on it. We love to work with talented and enthusiastic developers. Get Trezor 2. Side channel attacks are not as difficult as many people think. Learn more about recovery. Step 1. Get your Trezor today. In this graphic the individual sha cycles are clearly visible except at the part where the power consumption of the display caused by displaying the progressbar muffles the signal of the processor.
They bitconnect to sale bitcoin paper storage available for purchase. At the time I did this work, I was not involved with Satoshi Labs or any of their competitors. If the site's scope is narrowed, poloniex ripple withdraw destination tags link coin ledger nano s should the updated help centre text be? By now, the price has risen to 73 EUR at amazon. Step 4. Basically, they use the fact that the microprocessor does unexpected things if power supply or the clock signal is broken. You will now choose your pin. It only takes 5 minutes. Please be advised ETH will be required for gas to move any tokens held in your old wallet. If you are coming from an old wallet and want your ETH and tokens on your new, secure Trezor address, you will need to send your funds to your new address through a regular transaction. The horizontal axis is the time in seconds, the vertical axis the voltage over the resistor. I don't think you can as nem price crypto best cryptocurrency for cheap reddit Trezor and every other hardware wallet does not expose your private keys to the computer it is connected to. Choose one out of the five that you like. Get your Trezor today. Please purchase hardware wallets from the original source. You cannot import your old MEW address into this, or use your old wallet with it. Trezor One. There are other attack vectors like fault injection that could still be used and may get around the PIN protection. Trusted by companies of all sizes. The goal was to measure power consumption of my TREZOR over time to see whether I can detect which code it is executing or even recover the private keys.
The goal was to measure power consumption of my TREZOR over time to see whether I can detect which code it is executing or even recover the private keys. In reaction to these results, PIN protection was added for computing public keys. The new firmware 1. You also need basic soldering skills south korean bitcoin price is there illegal porn on bitcoin deep knowledge about the code that is running. Unicorn Meta Zoo 3: Endorsed by experts. Trezor Model T. Encrypted storage on cloud. However, the fingerprint is close enough to recognise it, even if the firmware is different. Also analysing electromagnetic radiation or acoustics shouldn't be feasible, as they have even less information. Again, do not write this phrase down on your computer. From here, send your ETH and tokens to your new Trezor address, ready to be accessed in a more secure fashion. A simple recording of one key derivation which can be done in a few seconds give you all the information you need from this TREZOR. Securing your digital assets has never been more straightforward. Thus it is highest in the area where the progress bar is displayed. No need. However, the exact timing build coin on ethereum reporting bitcoin capital gains the function still depends on the input. It is nearly impossible to get any information about the actual values used in the SHA computation.
This can be achieved by accessing your old wallet through MEWconnect, MetaMask, Keystore file, or private key however you usually did it before the Trezor. Although the code is not perfect, it should make side-channel attacks much more difficult. Ask Question. Don't risk your coins. Love my model T! You also need basic soldering skills and deep knowledge about the code that is running. Make your coins safe again. No need. Pick your own Trezor. It leaves out some crucial steps in order to make it not too simple for anyone reading this page. The later steps get even easier; for them only 5. Join the community of satisfied users around the world. You are in good company. The recovery seed follows a standard created by us at SatoshiLabs, but it is widely used, compatible with many wallet apps. A screen will pop-up asking for you to allow MEW permissions to read the public keys from your Trezor device. Until firmware 1. Stackexchange to questions applicable to…. By using our site, you acknowledge that you have read and understand our Cookie Policy , Privacy Policy , and our Terms of Service.
If the TREZOR is not passphrase protected, it wakes up, computes the master private key from the seed and then the public key from the private key. At this time the function will have processed only a few of the lowest bits of the private key. Although the single cycles are clearly visible, they look very similar. It has its own private key, encrypted into the device. This should make it impossible to recover any information about the private key. When zooming close into the different parts, one can distinguish the PBKDF-2 algorithm from the part where bitcoin cash eda localbitcoins usd public key is computed. Hardware wallets bought off ebay or from other vendors cannot be guaranteed secure. By using our site, you acknowledge that reddit ethereum laughing cow guide to bitcoin hard fork have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. Since an oscilloscope can only measure voltage, I inserted a 10 Ohm resistor for 0. If your TREZOR gets stolen and it has no yobit wallet maintenance cheapest hardware bitcoin wallet protection or if the passphrase is weakyou should transfer the coins to a different wallet.
In reaction to these results, PIN protection was added for computing public keys. In the above graphics, there are four spikes, which mark the start of the bip32 derivation steps. Also you can see clearly see the regular cycle caused by the 90 Hz refresh rate of the display. During this period, the power consumption of the processor is higher than when the algorithm pauses to refresh the display which it does eight times. The Initial Set-Up Step 1. Therefore, I investigated whether it is possible to use a side channel to recover the private key from the public key computation. If you are coming from an old wallet and want your ETH and tokens on your new, secure Trezor address, you will need to send your funds to your new address through a regular transaction. Bitcoin Stack Exchange works best with JavaScript enabled. This is the name you will see on your device whenever you plug it in. Led by renowned experts of the crypto industry. Learn from Trezor Developer's Guide. This is from the first part of pbkdf, where the progressbar is not yet filled. Hardware wallets bought off ebay or from other vendors cannot be guaranteed secure. Although the code is not perfect, it should make side-channel attacks much more difficult. Unbox your Trezor! You can also access other networks, such as Ethereum Classic ETC , by choosing the related network path. There are other attack vectors like fault injection that could still be used and may get around the PIN protection. However, the time these operations take is too short to be visible. The horizontal axis is the time in seconds, the vertical axis the voltage over the resistor.
This is the name you will see on your device whenever you plug it in. My best guess is that because I removed some duplicated code, the same code path is used throughout the inner loop, while the previous code switched between the u vertcoin electrum bitcoin pools that support gui miner even and v is even code paths, depending on the input. Do not write this phrase down on your computer, do not take a picture of the phrase. Email Required, but never shown. The recovery seed follows a standard created by us at SatoshiLabs, but it is widely used, compatible with many wallet apps. In this graphic the individual sha cycles are coinbase no email for device verification pay bitcoin with credit card visible except at the part where the power consumption of the display caused by displaying the progressbar muffles the signal of the processor. How do we grade questions? In the end there are best bitcoin sites bitcoin scratchoff few multiplications, that will again form two regular small spikes followed by a big spike, where the next point addition starts. The later steps get even easier; for them only 5. It may be possible to recover more information by opening the device and measuring the power consumption directly at the processor.
By now, the price has risen to 73 EUR at amazon. What About My Old Wallet??? However, the time these operations take is too short to be visible. You can also access other networks, such as Ethereum Classic ETC , by choosing the related network path. It took only a single recording of the computation of the public key, to recover the private key. Use pen and paper. In the end there are a few multiplications, that will again form two regular small spikes followed by a big spike, where the next point addition starts. Visit trezor. After these cycles, the computation of the public key begins.
We love to work with talented and enthusiastic developers. Home Questions Tags Users Unanswered. Your entire wallet is always accessible via your personal 12 to 24 words long recovery seed. There are other attack vectors like fault injection that could still be used and may get around the PIN protection. It only takes 5 minutes. This is how you can still securely spend your Bitcoin blockchain ethereum ether ethereum vs bitcoin core with a computer that has malware on it. Trusted by companies of all sizes. Now you will be prompted to choose a name for your Trezor. The power consumption of the display depends on the number of white pixels in the current line. Side channel attacks are not as difficult as many people think. Hardware wallets bought off ebay or from other vendors cannot be guaranteed secure. This should prevent most side-channel attacks.
This is how you can still securely spend your Bitcoin even with a computer that has malware on it. This is a particularly interesting function, since the code it is executing is dependent on the input and it looks different for every input, with which it is called. It may be possible to recover more information by opening the device and measuring the power consumption directly at the processor. The power consumption goes slowly down at these places. At this time the function will have processed only a few of the lowest bits of the private key. Join us and work on top-notch global projects related to Bitcoin and security. However, I could not detect a difference between cache hit or miss with my hardware. It has its own private key, encrypted into the device itself. Step 3. Although the single cycles are clearly visible, they look very similar. Narrow topic of Bitcoin. This is one of the most important steps. You will be choosing a new ethereum address on this device, and using it as your new main wallet. The power consumption of the display depends on the number of white pixels in the current line. Invented for your digital freedom. However, also the generation of the public key may leak some information via a side channel. Until firmware 1.
However, I could not detect a difference between cache hit or miss with my hardware. It is nearly impossible to get any information about the actual values used in the SHA computation. The small distortions are probably caused by the display. Attach your Trezor device and head to MEW. You will see a list of addresses. A screen will pop-up asking for you to allow MEW permissions to read the public keys from your Trezor device. I have recovered bits of a private key as a proof of concept. They are not reliable. Securely via computer or mobile. However, the fingerprint is close enough to recognise it, even if the firmware is different. Featured on Meta. The exact fingerprint depends on the exact firmware, though. Usually the discussions of side-channel attacks mention the code that signs a Bitcoin transaction. I don't know that I would ever want to do that but I am just curious.. If you are coming from an old wallet and want your ETH and tokens on your new, secure Trezor address, you will need to send your funds to your new address through a regular transaction. Also analysing electromagnetic radiation or acoustics shouldn't be feasible, as they have even less information. You will now choose your pin. I don't think you can as the Trezor and every other hardware wallet does not expose your private keys to the computer it is connected to.
The later steps get even easier; for them only 5. Also, if you have passphrase protection, this attack does not work even with firmware 1. However, an unscrupulous attacker may just break open the case and rip off the display to achieve the same effect. During this period, the power consumption of the processor is higher than when the algorithm pauses to refresh the display which it does eight times. You can also access other networks, such as Ethereum Classic ETCby choosing the related network path. MEW will bring you back arch bitcoin spiritual calibration for bitcoin a page showing different networks and derivation paths. After these cycles, the computation of the public key begins. Post as a guest Name. If your TREZOR gets stolen and it has no passphrase protection or if the passphrase is weakyou should transfer the coins to a different wallet. This is from the first part of pbkdf, where the progressbar is not yet filled.

Trezor made a clear and easy to follow guide on how to restore your Trezor device here. Post as a guest Name. Featured on Meta. On average one has to check Step 6. It took only a single recording of the computation of the public key, to recover the private key. Each cycle contains two spikes, which are caused by the lines above and below the progressbar. Step 3. Therefore, I investigated whether it is possible to use a side channel to recover the private key from the public key computation. The power consumption goes slowly down at these places. It only takes 5 minutes. Why did this happen? We recommend holding. The Initial Set-Up Step 1. However, the fingerprint is close enough to recognise it, even if the firmware is different. Generating, and thus exposing, the private key using the seed words would be very foolish. This is how you can still securely spend your Bitcoin even with a computer that has malware on it. I have recovered bits of a private key as a proof of concept.
Until firmware 1. The ledger wallet ethereum eos gatehub 20 xrp free seed words should never be entered on a connected computer or device, just keep them safe off line. Hot Network Questions. If you are coming from an old wallet and want your ETH and tokens on your new, secure Trezor address, you will need to send your funds to your new address through a regular transaction. On the bright side, this simple side channel attack can be mitigated by using constant-time code and as I showed this code does not have to be slow. Trusted by companies of all sizes. Thus it is highest in the area where the progress bar is displayed. Do not write this phrase down on your computer, do not take a picture of the phrase. Post as a guest Name. Join us and work on top-notch global projects related to Bitcoin and security. Learn more about recovery. From here, send your ETH and tokens to your new Trezor address, ready to be accessed in a more secure fashion. The later steps get even easier; for them only 5. I don't think you can as the Trezor fastest deposit on coinbase put funds into bittrex every other hardware wallet does not expose your private keys to the computer it is connected to. A simple power analysis requires only a simple oscilloscope and that can hardly be called expensive laboratory equipment.
In this section I will therefore look into the key generation. Get Trezor 2. During this period, the power consumption of the processor is higher than when the algorithm pauses to refresh the display which it does eight times. How do we grade questions? Led by renowned experts of the crypto industry. Pick your own Trezor. Your entire wallet is always accessible via your personal 12 to 24 words long recovery seed. Sign up or log in Sign up using Google.