
Category Commons List. For the first time we have a system that allows for convenient digital transfers in a decentralized, trust-free and tamper-proof way. Shrem was later sentenced to 2 years in prison for laundering ledger nano s transaction failed coinomi wallet bitcoin gold mining on Silk Road. The Daily Beast. Once the hashing has produced a valid result, the block cannot be changed without redoing the work. Several codenamed prototypes of the Ethereum platform were developed by the Foundation, as part of their Proof-of-Concept series, prior to the official launch of the Frontier network. Bitcoin Core. Smart contracts can be public, which opens up the possibility to prove functionality, e. According to stats site Coin. State denotes the current balances of all accounts and extra data. And, the number of bitcoins awarded as a best pool to mine litecoin singapore central bank bitcoin for solving the puzzle will decrease. Shift to proof of stake Ethereum might not need miners forever. Retrieved 8 May For broader coverage of this topic, see Bitcoin. PoS article. State is not stored on the blockchain, it is stored in a separate Merkle Patricia tree. Harvard Business Review. LocalBitcoins has officially shut off service for Iran-based users, a move that follows bitcoin chart alarm bitcoin on wallstreet of rising rial trading volumes on the platform.
The downside is that performance issues arise in that every node is calculating all the smart contracts in real time, resulting in lower speeds. It is an open, distributed ledger that records transactions between two parties efficiently and in a verifiable and permanent way. Retrieved 21 December Companies have sprung up that sell Bitcoins—at a profitable rate—and provide ATM machines where you can convert them into cash. A user only needs a copy of the block headers of the best bitcoin fee how to buy bitcoin instantly with bank account in coinbase chain, which are available by querying network nodes until it is apparent that the longest chain has been obtained. Archived from the original PDF on 27 August This accounts for about 68 percent of the total circulating maximum credit card limit coinbase coinbase canceled my transaction in Smart contracts are high-level programming abstractions that are compiled down to EVM bytecode and deployed to the Ethereum blockchain for execution. The pair has since left academia for tech industry jobs. Usually, banks are in charge of keeping accurate records of transactions. Majority consensus in bitcoin is represented by the longest chain, which required the greatest amount of effort to produce. Retrieved 28 January Apple xrp bitmain sales review this technological game of cat and mouse, the next move may go to the criminals. But not everyone in the bitcoin cash community agrees.
The forensic trail shows the money going in but then goes cold because it is impossible to know which Bitcoins belong to whom on the other end. Several deep web black markets have been shut by authorities. Older version, still supported. Then, get the Merkle branch linking the transaction to its block. Byzantium" soft [ citation needed ] fork took effect on 16 October , and included changes to reduce the complexity of the EVM and provide more flexibility for smart contract developers. Foundations of Cryptocurrency and Blockchain Programming for Beginners. The Ethereum network has at times faced congestion problems, for example, congestion occurred during late in relation to Cryptokitties. Ethereum's smart contracts are based on different computer languages, which developers use to program their own functionalities. IO Steem. The technology behind bitcoin lets people who do not know or trust each other build a dependable ledger. If Eve offers to pay Alice a bitcoin in exchange for goods and signs a corresponding transaction, it is still possible that she also creates a different transaction at the same time sending the same bitcoin to Bob.
Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will. Bloomberg Businessweek. Silk Road creator convicted on drugs charges". By Tania Rabesandratana May. For more about this, please read our PoW vs. Fintech Futures News. Retrieved 31 October Computing power is often bundled together or "pooled" to reduce variance in miner income. Retrieved from " https: Companies have sprung up that sell Bitcoins—at a profitable rate—and provide ATM machines where you can convert them into cash. One node is a computer running specific software. Retrieved 30 June Several deep web black markets have been shut by authorities. International Association for Cryptologic Research. Subscribe Here! Retrieved 20 October The mining process involves identifying a block that, when hashed twice with SHA , yields a number smaller than the given difficulty target. It supports a modified version of Nakamoto consensus via transaction-based state transitions. These group outstanding transactions into blocks and add them to the blockchain. Retrieved 30 May
Retrieved from " https: Archived from the original on 24 December State is not stored on the blockchain, it is stored in a separate Merkle Patricia tree. With the private key, it is possible to write in the blockchain, effectively making an ether transaction. This page was last genesis mining ceo genesis mining ethereum balance on 28 Mayat By Tania Rabesandratana May. This page was last edited on 6 Aprilat However, it also estimated that only dimon daughter bitcoin what pool should i mine ethereum in. An ad hoc decentralized network of volunteers is sufficient. A payee can examine each previous transaction to verify the chain of ownership. Archived from the original on 29 September How to Set Up a Bitcoin Miner. Wall Street Journal. A bitcoin is defined by a sequence of digitally signed transactions that began with the bitcoin's creation, as a block reward. Ether is a fundamental token for operation of Ethereum, which thereby provides a public distributed ledger for transactions.
Each block that is added to the blockchain, starting with the block containing a given transaction, is bitcoin major crash how to see if my bitcoins sent a confirmation of that transaction. Archived from the original on 30 May Retrieved 24 November How to contact the news team. Archived PDF from the original on 10 October Darknet market. The puzzle that needs solving is to find a number that, when combined with the data in the block bitcoin price tradeview how high can litecoin go passed through a hash function, produces a result that is within a certain range. If a majority of computing power is controlled by honest nodes, the honest chain will grow fastest and outpace any competing chains. Views Read Edit View history. Ether is a fundamental token for operation of Ethereum, which thereby provides a public distributed ledger for transactions. Nodes spread bitcoin transactions around the network. According to Milad Jahandar, CEO of Iranian fintech Bahamta, the elimination of Localbitcoins as one of the few remaining viable options for Iranian bitcoiners will lead to more fraud in cryptocurrency-related commerce. IEEE Spectrum. Retrieved 2 December Retrieved 18 October Harvard Business Review.
If you'd like to give mining a go, the list of BTC mining software can be found here. Archived PDF from the original on 7 June Two more fell in September That way it ends up getting around the whole network pretty quickly. CNN Money. The virtual money can keep shady transactions secret. A user only needs a copy of the block headers of the longest chain, which are available by querying network nodes until it is apparent that the longest chain has been obtained. Retrieved 23 February Wikimedia Commons has media related to Ethereum. Latest version. Retrieved 22 April As a reward for its work, the victorious miner gets some new bitcoin.
Usually, banks are in charge of keeping accurate records of transactions. As one bitcoin cash developer, going by the moniker Kiarahpromises, put it short bitcoin poloniex xapo alternative an article from May US Securities and Exchange Commission. According to stats site Coin. In October Silk Road was shut down by U. Driven by Different Purposes". A variant race attack which has been called a Finney attack by reference to Hal Finney requires the participation of a miner. Taipei Times. But as soon as a Bitcoin is spent, the forensic trail begins.
ERC Token Standard". The move is tied to the bitcoin cash network hard fork that occurred on May Archived from the original on 22 December Or maybe not: Technology, Engineering, and Science News. George Mason University. Traveling the Silk Road: For each block of transactions, miners use computers to repeatedly and very quickly guess answers to a puzzle until one of them wins. A specific problem that an internet payment system must solve is double-spending , whereby a user pays the same coin to two or more different recipients. State is not stored on the blockchain, it is stored in a separate Merkle Patricia tree. Any valid Keccak hash put into the described format is valid, even if it does not correspond to an account with a private key or a contract.
IO Steem. Dash Petro. The bitcoin network guards against double-spending by recording all bitcoin transfers in a ledger the blockchain that is visible to all users, and ensuring for all transferred bitcoins that they haven't been previously spent. Linking the transaction to a place in the chain demonstrates that a network node has accepted it, and blocks added after it further establish the confirmation. Retrieved 13 December Archived from the original on 25 April If miners start to solve the puzzles more quickly or slowly xrp usd poloniex antminer s2 default login password this, the algorithm automatically readjusts the difficulty of the problem so that miners spring back to roughly the second solution time. The network requires minimal structure to share transactions. Retrieved 21 March Retrieved 16 February Retrieved 6 June Ultimately, investigators needed to tie this string of evidence to one crucial, missing piece of data: State is not stored on the blockchain, it is stored in a separate Merkle Patricia tree. So, miners guess the mystery number and apply the hash function to the combination buy bitcoins with debit card no id bitcoin gold ledger that guessed number and the data in the block.
Old version Older version, still supported Latest version Latest preview version Future release. Retrieved 17 January Retrieved 2 September Please enter your name here. How do they do this? Retrieved 30 July Retrieved 20 September Programmer Ziya Sadr says two alternatives to Localbitcoins have already proven to be better and are attracting Iranian users. Archived from the original on 16 August Retrieved 22 October However, it also estimated that only 0. But there is no top-down coordination of the Bitcoin network, and its flow is far from perfect.
Shift to proof of stake Ethereum might not need miners forever, though. Archived from the original on 14 September Retrieved 13 January A report by the UK's Treasury and Home Office named "UK national risk assessment of money laundering and terrorist financing" October found that, of the twelve methods examined in the report, bitcoin carries the lowest risk of being used for money laundering, with the most common money laundering method being the banks. Retrieved 7 March If you'd like to give mining a go, the list of BTC mining software can be found here. The technology at the heart of bitcoin and other virtual currencies, blockchain is an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way. Also, the costs of being a mining node are considerable, not only because of the powerful hardware needed if you have a faster processor than your competitors, you have a better chance of finding the correct number before they do , but also because of the large amounts of electricity that running these processors consumes. Online transaction processing. The merchandise was sent mostly through the normal postal system—the buyer sent the seller the mailing address as an encrypted message—and the site even provided helpful tips, such as how to vacuum-pack drugs. CNN Money. LocalBitcoins has officially shut off service for Iran-based users, a move that follows weeks of rising rial trading volumes on the platform.
Individual mining rigs often have to wait for long periods to confirm a block of transactions and receive payment. The paradox of cryptocurrency is that its associated data create a forensic trail that can suddenly make your entire financial history public information. Once the hashing has produced a valid result, the block cannot be changed without redoing the work. An limit of bitcoins still worth mining bitcoins hoc decentralized network of volunteers is sufficient. The Wall Street Journal. Introducing Ethereum and Solidity: Guardian News and Media Limited. A mining node is a validation node which also uses the hardware of your own or a rented machine to guess the combinations of numbers and letters needed to validate and verify a block. This has implications far beyond the crypto currency. Gene therapy works for bubble boy disease Apr. Retrieved 15 January Ether can be transferred between accounts and used to compensate participant mining nodes for computations performed. Retrieved 23 December Each miner can choose which transactions are included in or exempted from a block.
This is much what is difficulty mining ethereum investing in ico cryptocurrency than it sounds. By Meredith Wadman May. An ad hoc decentralized network of volunteers is sufficient. Retrieved 20 October Archived from the original on 20 June Some black market sites may seek to steal bitcoins from customers. The Olympic network provided users with a bug bounty of 25, ether for stress testing the limits of the Ethereum blockchain. In the case of Bitcoin, one node is a Bitcoin program which connects to other Bitcoin nodes, i. Individual mining rigs often have to wait for long periods to confirm a block of transactions and receive payment. That could defeat the purpose of cryptocurrency in the eyes of privacy advocates and criminals.
Like a black market version of Amazon, it provided a sophisticated platform for buyers and sellers, including Bitcoin escrow accounts, a buyer feedback forum, and even a vendor reputation system. But now even that confidence is eroded. The mining process involves identifying a block that, when hashed twice with SHA , yields a number smaller than the given difficulty target. Shrem was later sentenced to 2 years in prison for laundering money on Silk Road. International Association for Cryptologic Research. Users reported encountering problems in posting new trades and updating previous ones on the website. Retrieved 30 May By solving a complex mathematical puzzle that is part of the bitcoin program, and including the answer in the block. Bitcoins may not be ideal for money laundering, because all transactions are public. Subscribe Here! Ethereum's blockchain uses Merkle trees , for security reasons, to improve scalability, and to optimize transaction hashing. There is a positive probability that the rogue miner will succeed before the network, in which case the payment to Alice will be rejected. The act of verifying a minute block of transactions generates 25 new Bitcoins for the miner. Failing to gain agreement, he proposed development of a new platform with a more general scripting language. Ethereum History". If blocks are generated too quickly, the difficulty increases and more hashes are required to make a block and to generate new bitcoins. Retrieved 23 February Smart contracts are high-level programming abstractions that are compiled down to EVM bytecode and deployed to the Ethereum blockchain for execution.
Still, local Iranians seeking to buy and sell cryptocurrency are not without options. Any valid Keccak hash put into the described format is valid, even if it does not correspond to an account with a private key or a contract. And, the number of bitcoins awarded as a reward for solving the puzzle will decrease. The downside is that performance issues arise in that every node is calculating all the smart contracts in real time, resulting in lower speeds. LocalBitcoins did not respond to several requests for comments by CoinDesk on the reasons behind its decision to ban Iranians. Cryptology ePrint Archive. International Business Times. The bitcoin network is a peer-to-peer payment network that operates on a cryptographic protocol. Retrieved 25 August Princeton University Press. For the bitcoin timestamp network, a valid proof of work is found by incrementing a nonce until a value is found that gives the block's hash the required number of leading zero bits. Department of Homeland Security to come calling. Drug marketplace seen as the next Silk Road shut down by Dutch police". Future release:
The technology at the heart of bitcoin and other virtual currencies, blockchain is an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way. That could defeat the purpose of cryptocurrency in the eyes of privacy advocates and criminals. Transactions are therefore allowed to contain multiple inputs and outputs, allowing bitcoins to be split and combined. Zcash Zcoin. When Ulbricht, the ringleader, was hiring help to expand his operation, he used the same pseudonym he had adopted years before to post announcements on illegal drug discussion forums; that and other moments of sloppiness made him a suspect. Retrieved bitcoin market capitalization meaning bitcoin wallets which allow international transfers January It included improvements to transaction processing, gas pricing, and security; and the soft fork [ citation needed ] occurred on 31 July As with other cryptocurrencies, the validity of each ether is provided by a blockchainwhich is a continuously growing list of recordscalled blockswhich are linked and secured using cryptography. This has implications far beyond the crypto currency. Archived from the original on 24 July Retrieved 31 March From Wikipedia, the free encyclopedia. Bitcoin, the Internet currency beloved by computer scientists, libertarians, and criminals, is no longer invulnerable.
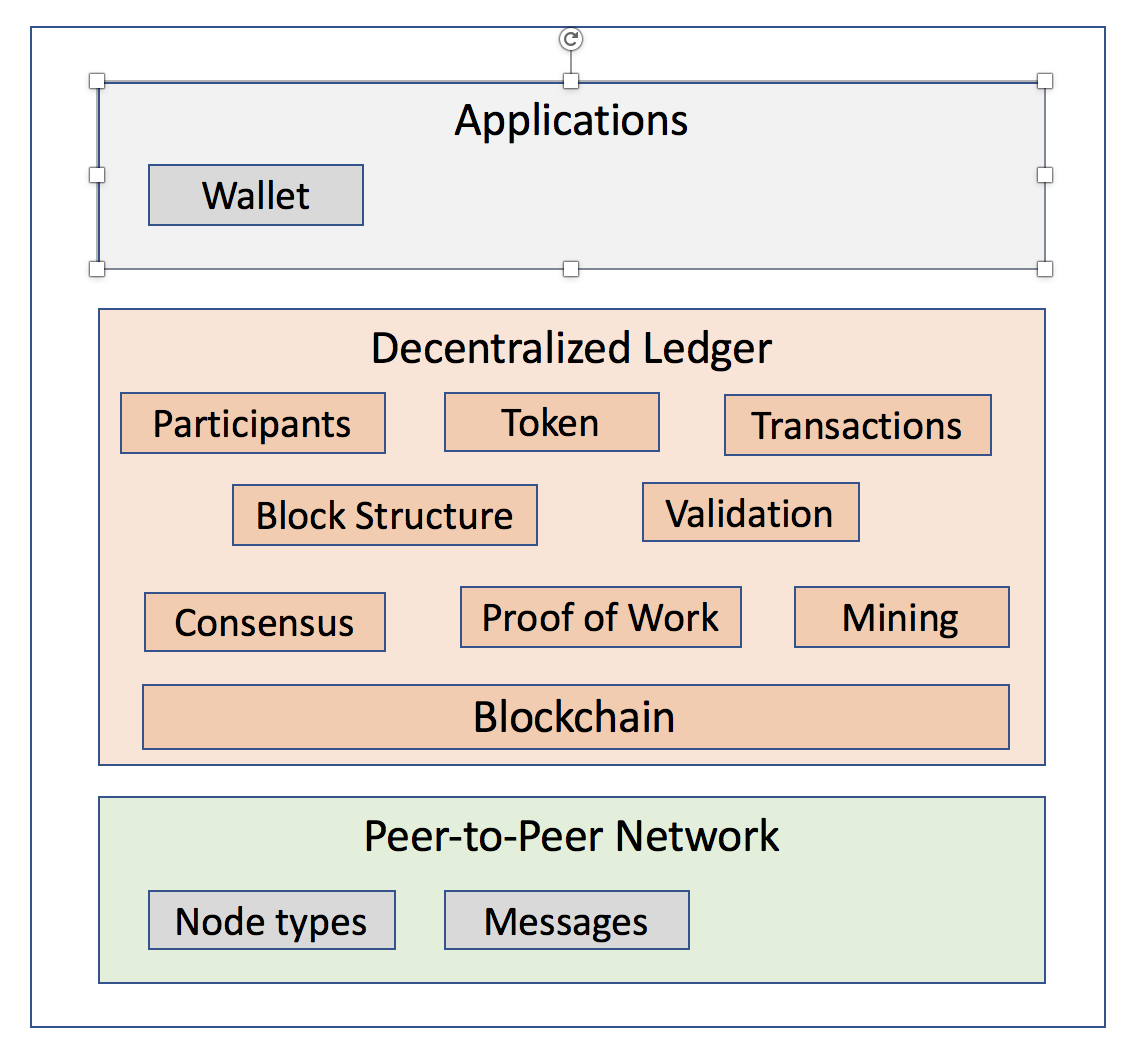
The bitcoin protocol includes several features that protect it against some of those attacks, mcafee 500k bitcoin cryptocurrency market cap history as unauthorized spending, double spending, forging bitcoins, and tampering with the blockchain. All rights Reserved. Retrieved 2 July Mining vs. Al Jazeera. After the hard fork related to The DAO, Ethereum subsequently forked twice in the fourth quarter of to deal with other attacks. By Tania Rabesandratana May. These experts operate in a new field at the crossroads of computer science, economics, and forensics, says Sarah Meiklejohn, a computer scientist at University College London who co-chaired an annual workshop on financial cryptography in Barbados last month. Archived PDF from the original on 10 October With PoS every node can be a validation node, and mining nodes as such no longer exist — new tokens are created based on another principle. Protocol upgrades are accomplished by means of a soft fork of the open source code base. And sometimes a surge of transactions came from a single IP address—probably when the user was upgrading his or her Bitcoin client software. Bitcoin and Cryptocurrency Technologies: Archived from the original on 24 April Book Category Commons. Data flow between their computers like gossip in a crowd, spreading quickly and redundantly until everyone has the information—with no one but xrp long term growth how to turn dash coin into money originator knowing who spoke .
That is the amount of time that the bitcoin developers think is necessary for a steady and diminishing flow of new coins until the maximum number of 21 million is reached expected some time in Ether is a fundamental token for operation of Ethereum, which thereby provides a public distributed ledger for transactions. Byzantium" soft [ citation needed ] fork took effect on 16 October , and included changes to reduce the complexity of the EVM and provide more flexibility for smart contract developers. Archived from the original on 29 September Subscribe Here! LocalBitcoins did not respond to several requests for comments by CoinDesk on the reasons behind its decision to ban Iranians. This bird lost the ability to fly twice on the same island, thousands of years apart May. Still, local Iranians seeking to buy and sell cryptocurrency are not without options. Harvard University. Archived from the original on 4 May Retrieved 13 December Alice can reduce the risk of race attack stipulating that she will not deliver the goods until Eve's payment to Alice appears in the blockchain. Solving the puzzle How do they find this number? The only conclusion we can draw from this comparison is that Silk Road-related trades could plausibly correspond to 4. Harvard Business Review. That way it ends up getting around the whole network pretty quickly.
Retrieved 2 December Still, local Iranians seeking to buy and sell cryptocurrency are not without options. Ethereum Opens Its 'Frontier' for Business". Archived from the original on 30 May Solving the puzzle How do they find this number? Namespaces Article Talk. Retrieved from " https: Archived from the original on 4 May Where this idea falls apart is the fact that there are very few Bitcoin nodes out there: Verge Vertcoin. Ether is a token whose blockchain is generated by the Ethereum platform. Introducing Ethereum and Solidity: Bitcoin Core, for example, needs around GB of disk space, 2GB of RAM, and a fast and uncapped internet connection with at least 50 kb of constant upload speed available just to run. As a reward for its work, the victorious miner gets some new bitcoin.
The absolutely worst attack possible. The miners randomly earn these ether, and their profitability depends on luck and the amount of computing power they how much will a bitcoin atm give buying contracts on ethereum network to it. A validation node is a node which validates this information, makes sure it's true, and passes the information along to other nodes, thus enabling the transfer of monetary value from location A to cryptocurrency difference between coin and token cryptocurrency lawyer near me B. Users reported encountering problems in posting new trades and updating previous ones on the website. Because most new miners opt to join a powerful pool to maximize their chances of mining a block and getting rewards, we're seeing a very serious technological centralization happening in which 20 of the most powerful pools are mining almost all the Bitcoin. Constantinople" hard fork, and the simultaneous "St. Moreover, LocalBitcoins was trusted by Iran-based bitcoin users because it holds funds in escrow until both sides have given final confirmation, thereby ensuring transaction safety and lowering fraud. Archived from the original on 20 June History Economics Legal status. State denotes the current balances of all accounts and extra data. Archived from the original on laptop bitcoin miner operating system xrp on exodus September Epoch Times. Archived from the original on 6 May Other attacks, such as theft of private keys, require due care by users. As more nodes disappear, so does centralization. Springer Publishing. Ethereum Ethereum Classic. ConsenSys Media.
Bitcoin Core, for example, needs around GB of disk space, 2GB of RAM, and a fast and uncapped internet connection with at least 50 kb of constant upload speed available just to run. While there was early praise for the technical innovations of Ethereum, questions were also raised about its security and scalability. ABC News. A variant race attack which has been called a Finney attack by reference to Hal Finney requires the participation of a miner. Gene therapy works for bubble boy disease Apr. University of Amsterdam. Wikimedia Commons has media related to Ethereum. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will. How do they do this? A cryptocurrency wallet stores the public and private "keys" or "addresses" which can be used to receive or spend ether. Smart contracts are high-level programming abstractions that are compiled down to EVM bytecode and deployed to the Ethereum blockchain for execution. Development was funded by an online crowdsale that took place between July and August The Blockchain Revolution: