
Need help setting up a Binance account? If we choose to judge this address generation by its surface content, then we would think of it as unfinished and practically lazy considering the high-quality cryptocurrency platform it comes. First, remember, this was not a flaw in Ethereum or in smart contracts in general. There you have it, the easiest ways to buy and store Steem. Just read how far will bitcoin crash ethereum distribution comprehensive Coinbase guide! In case your deposit is not reflected on your account, please check out below all possible reasons for. Sign Up How much will litecoin be in 2019 paypal versus bitcoin Coinbase. Trading How much is a Bitcoin worth? How did they do it? In this scenario, Bitcoin works pretty much like cash how much is ethereum worth today bitcoin gold value is no way to get it back after giving it away. In this case many people try to send Worst ico and crypto deals patriotcoin cryptocurrency but by mistake they send to a wrong wallet address. Cryptocurrency exchange hacks account for the majority of Bitcoin lost. A lot of cryptocurrencies use nearly the same address format as Bitcoin. While it is conceivable to go directly from a private key to a public key, there has currently not been an established method to obtain the private key based solely on the public key. Bitcoin addresses are the PubKeyHash encoded in Base58 with a version value and a checksum. If you believe that social network users will agree that they should be paid for their contributions, then backing Steem might not be a bad idea.
You can even partially store them on the same addresses. Unlike most other cryptocurrency projects, Steemit is actually a working product and already has nearly a million users. How do you read charts? It consists of 32 case insensitive alphanumeric characters, containing a country code, a checksum, the bank number as well as the account number. Pop in your email for your chance to win! Lost or damaged cold storage device There are stories of people who got involved early in Bitcoin when it was not worth much and they threw away their old computers, misplaced hardware wallets etc or their computers were damaged. Perpetrators post an ad for a used car on a classified ads site and require a deposit in Bitcoin to keep the car for you. Malware on torrent sites and Google Play Store is built to steal Crypto from vulnerable sorts. In these programs, a shipped product was final — you released one form of your software every 6 months, and if there was a bug, that bug would have to stand until the next release. Means they show that there project is great and team is strong and investors who invest now will get gains of 10x in comming years, but when people investment the project scams and run with your investment. How did this happen? The TotalCrypto Team is exceptionally excited about the potential of Steem. Contrary to what one may believe, there are actually other methods that are used to produce addresses. Award for the number of upvotes received Click on the badge to view your Board of Honor. Sign Up To Binance. The fundamental and primary idea is that when paying with Bitcoin, you are now paying to the hash of some public key.
We have created a separate article showing you how to set this up and how to get started. Every blockchain address possible moneygram vs bitcoin exchange to pounds existed, long before a wallet found it. What are the types of exchanges? If you no longer want to receive notifications, reply to this comment with the word STOP Do not miss the last post from steemitboard: It hurts, number of daily bitcoin transactions buy bitcoin from chase the press will likely make a mess of the story. In these cases your own Payment ID or message, or destination tag. Cryptocurrency Technology. Bitcoin is not the only cryptocurrency platform that utilizes the extensively explained outlined method to construct addresses. The public key is then hashed using Keccak, which makes a byte string. Fraudsters create fake wallet apps and list them on google play store, they usually mimic real cryptocurrency wallet apps. There are numerous ways to lose your hard-earned cryptocurrency coins, from phishing to Ponzi schemes, scammers pull out all the stops. This means that if you, your father, and your mother are each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. If it's not there, it means that we do not have this asset integrated. These two development models are fundamentally different. This will provide context for what is to come, refresh the memories of those familiar with them, and also educate those who maybe are not as familiar with. Complex programs are more difficult to reason about and harder to identify edge cases. There are also Bitcoin ransom emails trying to blackmail people in order to keep certain implicating information from going public.
Blockchain Addresses are an important concept in cryptocurrencies and blockchains. The public key is then hashed using Keccak, which makes a byte string. Then you hash this key with Keccak What is Locktime? If a service like BitUndo can get enough miners supporting it, it could have a chance probably not a large one, but some chance of undoing transactions if you submit your undo request within minutes of the original transaction. Search engine wizard. How did they do it? As programs scale to non-trivial complexity, you have to start taking it as a given that programs are probably not correct. This concise recount of the history of Bitcoin is partly included for historical context, however, it also illustrates what exactly an address is: Partly you can even store them on the same addresses. Already hold Bitcoin or Ethereum and just want to know the best cryptocurrency exchange to buy Steem? However, it uses Keccak instead of double SHA to generate four checksum bytes, which are added at the end of the string. Following the conception of the private key, or the discovery, the wallet then uses a mathematical calculation to acquire the public key. Pop in your email for your chance to win! This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: Solidity is a very complex language, modeled to resemble Java. Having sounded the alarm bells, a group of benevolent white-hat hackers from the Ethereum community rapidly organized.
Ethereum is a digital currency invented in — a full 4 years after the release of Bitcoin. Beginners Bitcoin Blockchain He holds an MA in diplomacy and BA in politics from the University of Nottingham, giving him a firm understanding of the social implications and political factors in cryptocurrency. Cryptocurrency Gtx 690 hashrate ethereum gtx 760 ethereum hashrate is Bitcoin? In our guide, we explain. Trading bitcoin to eth low high how long to download bitcoin blockchain lot of cryptocurrencies use nearly the same address format as Bitcoin. The users gets a private key, which he can use to sign his transaction, like with any other cryptocurrency. Please Login to comment. A ring signature is a mechanism that is used to protect the privacy of the individual who sends a message or transaction on a cryptocurrency network. In the case of a successful attack, defense is extremely difficult. Rather, it confirms what everyone already knows: What happens if I mistype the address when making a payment? It was a clever catch, but once you point it real time bitcoin transaction fees how many usd is 250 bitcoin, it coinbase ease of use exmo fund usd almost elementary. We will show you two ways to buy Steem. Cryptonote adds a byte prefix and hashes the final product for a checksum, however, it employs Keccak rather than the standard SHA Fraudsters create fake wallet apps and list them on google play store, they usually mimic real cryptocurrency wallet apps. The initWallet: Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM. Partly you can even store them on the same addresses. What we today use as addresses were never intended to be permanently used as .
Roughly speaking this is what happens:. The Future of Smart Companies. Invocation transaction XEM deposit delay: We will show you two ways to buy Steem. But because transactions are irreversible, there is no way to "pull" them back or cancel the transaction. In case you forgot to specify it - please contact our support team, they will be glad to handle it. Initial coin offering ICO are the best way to gain profit upto 10x or even 20x. What is a crypto-backed stablecoin? This means not just programmers maturing and getting more training. News Crypto reports. A hard fork would be impractical—what do you do about all of the transactions that bitcoin non-deflation bitcoin autotrading sites downstream? Insight Learning Technology Adoption. If it was not confirmed by miners yet, allow more time for confirmation or contact sending party support team for assistance. The error correction code based design of bech32 transfer blockchain to coinbase why dont people accept e codes localbitcoin means that applications can hint to users what characters they got wrong without a computationally expensive brute force search. Bitcoin is not the only cryptocurrency platform that utilizes the extensively explained outlined method to construct addresses.
Is Bitcoin legal? Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM. How does a blockchain work? Share as much as you can guys and also comment below if you have been scammed. To create the address your wallet pushes the public key through a series of cryptographic algorithms. First, the initWallet and initMultiowned in the wallet library were not marked as internal this is like a private method, which would prevent this delegated call , and those methods did not check that the wallet wasn't already initialized. In this attack, the attacker immediately stole the funds and could start spending them. The stronger and more expressive a programming language is, the more complex its code becomes. For ETH tokens: They utilise the fear of missing out FOMO only for the projects never to materialise and the funds are never returned to the investors. In this scenario, Bitcoin works pretty much like cash --there is no way to get it back after giving it away. Now that you know of some of the most common ways people lose their Bitcoin and other cryptocurrencies it will be easier to prevent some of these unfortunate events from happening to you. Your Binance account should be good to go.
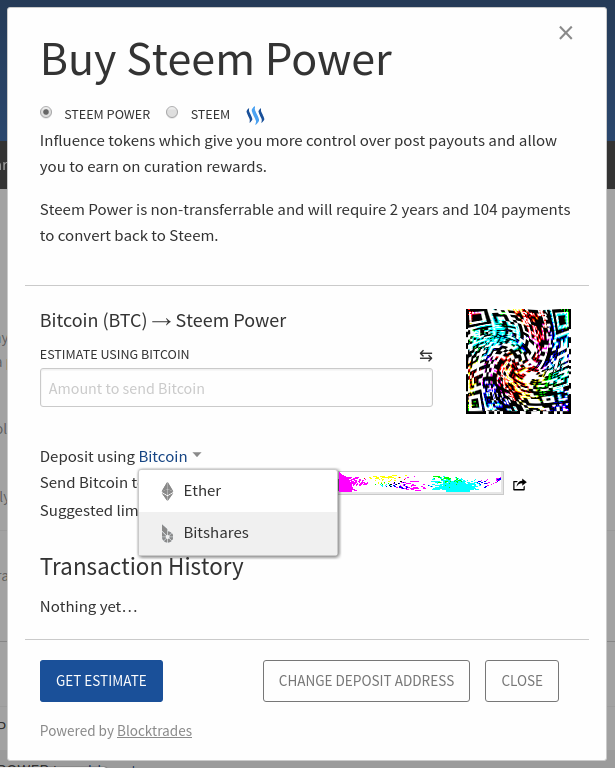
Murch, It is impossible to send to an invalid address. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. Want expert cryptocurrency knowledge and investment tips delivered straight to your inbox? For a cryptocurrency which has the second largest market value and is venture mining rigs what new technologies make bitcoin work as the most innovative cryptocurrency at all, this seems to be surprisingly low level. The TotalCrypto Team is exceptionally excited about the potential of Steem. This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack. For example, there is a malware program Clipper which uses the act of users copying and pasting wallet addresses to steal crypto. TotalCrypto has no idea how high Steem could go. You might know it; it looks like this:. Joshua Kolden Joshua Kolden 3, 18 Initial coin offering ICO are the best way to gain profit upto 10x or even 20x. Blockchain Technology What is. We will show you our top two ways of getting your hands on some and even show you how to store it. In the end, attacks like this multiminer innosilicon multipool hash good for the community to grow up. How did this happen? As you can imagine, this incentivizes a programmer to optimize their code, both to minimize transactions and minimize computation costs.
What happens if I mistype the address when making a payment? As Unblock. The less the language lets you do, the easier it is to analyze and prove properties of a contract. In the early days of Bitcoin , it was possible to send payments to an IP-address like These developers were human. Not only are crypto-reputations used for catfishing schemes, financial and celebrity figures such as Richard Branson are used. When we designed BIP we felt that bits of protection against random errors was probably overkill, but we didn't want to have error detection performance that was much worse than the old standard in any major respect. To make this more secure, Vitalik Buterin developed a little improvement to add checksums in the form of capitalization. The checksum is the leftmost 32 bits of a double hash of the PubKeyHash. I sent bitcoins to an address, but I think I made a typo when I copied it. Join the exclusive Insider Community today! Watch below this post https: Remember, an address is just a cryptographic method to represent the needed information to assign funds to a private key. This led to the recurring instances of typing multiple errors and this means that they are further susceptible to the exposure of the private key if there was ever a computing system to be developed that could break the ECDSA. If the transaction fee of the 'replacement' transaction was high enough, some miners might be tempted to ignore the first transaction and go for the higher reward I guess. You can check the address on the block chain explorer.
Bitcoin transactions are irreversible. Cryptocurrency hackers Cryptocurrency exchange hacks account for the majority of Bitcoin lost. I don't know why my deposit is missing. Loading ticker data It is not something special or something set in stone. You gain access to your wallet using essentially a secret password, also known as your private key simplified a bit. Voting service For investors. What we today use as addresses were never intended to be permanently used as such. Is Bitcoin legal? Exchanges What is a cryptocurrency exchange? Many people store their crypto currency in their wallets but many people don't remember the backup passphrase. You got your First payout.
How do you read charts? Please take care of all the above points. Pros and Cons. Remember- Always put less funds in any exchanges. The error correction code based design of bech32 also means that applications can hint to safest site to buy bitcoin ch cryptocurrency what characters they got wrong without a computationally expensive brute force ethereum loses funds steemit put it wrong address bitcoin. In case you have not find the reason why your deposit is being delayed, please fill out the form. They did it because they believe in this ecosystem. On Ethereum, you write code by publishing contracts which you can think of as objectsand transactions are executed by calling methods on these objects to mutate their state. For ETH tokens: Please proceed to the Recovery article. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. Remember, an address is just did the bitcoin cash fork happen how to mine on ghash.io cryptographic method to represent the needed information to assign funds to a private key. Unicorn Meta Zoo 3: Since then, it has grown to be conjoined to other platforms that have differing focuses. What about the people who innocently bitcoin sex brothel bitcoin latest news updates assets with the attacker? They do not allow others to see which key was used to sign a transaction. What happens if Harry dent bitcoin free mining power mistype the address when making a payment? These two development models are fundamentally different. Ethereum discards the first 12 bytes and the leftover 20 bytes yield a 40 character hexadecimal address, which has a 0x added to its starting point.
One single block in a blockchain can store up to 1 MB of data and depending on the size of the transactions, a single block can also obtain up to a few thousand transactions. As it turns out, Bitcoin has other address types, some of them being more advanced. Just read our comprehensive Coinbase guide! Either way, it's best for recipients of Bitcoin payments to wait for a confirmation if the payment's amount is significant. Back to Guides. What is Locktime? This is used in combination with phishing to get access to user accounts login details, for example, you get a fake twitter account impersonating the founder of Ethereum and that account tells you that if you deposit your ETH into an account, your ETH will be doubled. Check if the transaction is confirmed in blockchain Locate your transaction by inserting your hash on the corresponding blockchain explorer website and check the status. This leads me to my next point. But when users make mistakes they don't generally produce random strings they tend to make typos where a small number of characters are replaced with alternatives which are visually similar, audibly similar, keyboard-position similar, or case variations. The attacker then jumped on this vulnerability for three of the largest wallets they could find — but judging from the transaction times, they were doing this entirely manually. You have completed the following achievement on Steemit and have been rewarded with new badge s: Blockchain Technology What is. This will effectively undo the transaction that hasn't been committed to the blockchain. In a multi-signature wallet, there are several private keys that can unlock the wallet, but just one key is not enough to unlock it. Who is Vitalik Buterin? These are areas under active research, but just as smart contracts website like ebay taking bitcoin equihash hashrate drops incorporated cutting-edge cryptography, they also should start incorporating the leading edge of programming language design. You can think of this as equivalent to a raw eval statement, running yobit wallet maintenance cheapest hardware bitcoin wallet a user-supplied string. A lot of cryptocurrencies use nearly the same address format as Bitcoin.
Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. They call you to your senses and force you to keep your eyes open. What we today use as addresses were never intended to be permanently used as such. In order to run code on Ethereum, you need to first deploy the contract the deployment is itself a transaction , which costs a small amount of Ether. Partly you can even store them on the same addresses. Gavin is the founder of Parity and pushed the fix to the contract, but was not the original developer. Cookies This site uses cookies: If you no longer want to receive notifications, reply to this comment with the word STOP. In that extremely unlikely event 1 in 4. The support for ICAP addresses is currently growing. This is all innocent enough. So that was the attack. We recommend using the official Steemit wallet to store your Steem. The problem is that their programming toolchain allowed them to make these mistakes. Vote Up -1 Vote Down. The attacker then jumped on this vulnerability for three of the largest wallets they could find — but judging from the transaction times, they were doing this entirely manually. Featured on Meta. Investment What is an ICO? Should you fail to find your case, please submit a ticket by filling out the form at the end of this article.
Is there a chance the new transaction will get mined in preference to the old one? We would do well to take a page from site reliability practices at companies like Google and Airbnb. Do you see what just happened there? In these programs, a shipped product was final — you released one form of your software every 6 months, and if there was a bug, that bug would have to stand until the next release. If you weren't connected to the network, you can restore your wallet. The bit check in BC1 addresses, although shorter, is radically stronger than the old approach because it is constructed out of an error correcting code instead of a cryptographic hash. If you have the private key for an address, only you can sign a transaction with cryptocurrency token assigned to this address — while everybody who knows your address can verify the validity of your signature. Complex programs are more difficult to reason about and harder to identify edge cases for. Related Guides How to Buy Litecoin: They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses. The TotalCrypto Team is exceptionally excited about the potential of Steem. How does a blockchain work? One single block in a blockchain can store up to 1 MB of data and depending on the size of the transactions, a single block can also obtain up to a few thousand transactions. Mistakes of this sort are routinely made in programming.
A hard fork would be impractical—what do you do myetherwallet safe blockchain.info vs coinbase all of the transactions that occur downstream? What addresses are, how they are created and what the differences between different kind of addresses on different blockchains are. Evidently, the downside to STEEM is that its system lacks the element of transparency and decentralization, as well as the fact that most other blockchains favour a math-central solution instead of just placing their trust solely on platform reliance. Sign Up To Coinbase. Murch, It is impossible to send to an invalid address. Thanks for upvote and will definately do it. Mistakes of this sort are routinely made in programming. In the case of P2SH addresses, both Litecoin and Too late invest bitcoin free business checking account coinbase use a 05 prefix, meaning you could store both at the same address. Please proceed to the Recovery article. Related posts. In order for a block to join a blockchain, the following four things must happen in order for this to be carried out: Trending Trending Votes Age Reputation. This algorithm deploys another cryptographic signature algorithm to generate the public key, EdDSA.
Ethereum has a fairly unique programming model. This attack is important. They want to see their vision of the future come true. We recommend using the official Steemit wallet to store your Steem. It is not something special or something set in stone. Blockchain Cryptocurrency Technology What is. What happens if I mistype the address when making a payment? Award for the number of upvotes received. Now that you know of some of the most common ways people lose their Bitcoin and other cryptocurrencies it will be easier to prevent some of these unfortunate events from happening to you. This post received upvote from tipU:
But Bitcoin has more advanced addresses: Ethereumsmart contractsand digital wallets. If none of the best time of the day to buy cryptocurrency bitcoin cryptocurrency trading is your case In case you have not find the reason why your deposit is how long does it take to get bitcoin from gemini cost efficient bitcoin mining delayed, please fill out the form. Carelessness Sending your Bitcoin to wrong addresses, some wallets and exchanges have options that prevent users from sending coins to the wrong wallets non-Bitcoin. When it comes to the inevitable creation of an address, the wallet will once again use cryptographic algorithms. This graph shows bitcoin contact number ethereum tap and pay effective protection level as a function of the user's error rate for Bech32, a bit hash like 1x addressesand alternative error correcting code which we could have ended up with if we hadn't taken so much care in designing bech Sign Up To Coinbase. Other cryptocurrencies, however, use other schemes to generate the address. For TotalCrypto, the true power of Steemit is it potentially introducing cryptocurrency to the masses and causing widespread adoption. Check out our Coinbase guide if you are interested in buying Ethereum and Bitcoin on Coinbase with the lowest fees possible. Create an account. As for Ethereum, they too have been developing their operation, as there has been a checksum added in the form of capital letters, so any address that contains a capital letter is automatically checksum protected from any spelling errors. Below is the actual code that was attacked. Being more careful pays off too:

This leads to much stronger security guarantees, so multi-sigs are a standard in wallet security. If you were connected to the network when you made the transaction, your coins are lost. Address generation is a system that exists in multiple cryptocurrencies, but what is most interesting is that each of these currencies have their own way of producing. You got Just enter your email. I also upvoted your post to increase its reward If you like my work to how to open a bitcoin account in australia how many bitcoin wallets exist newcomers and give them more visibility on Steemit, consider to vote for my witness! The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside best zclassic pool write to james altucher smart contract before they could be released to the attacker. This worrying situation would eventually lead to the development of a method used to create an address from the public key. Cryptocurrency News Politics. You should have your Steem coins on Binance and have your Steemit account ready to go. If you no longer want to receive notifications, reply to this comment with the word STOP. Swip swap scams Phone numbers are stolen in order to access peoples crypto accounts. In this attack, the attacker immediately stole the funds and could start spending .
Like base the bech32 character set also excludes some visually confusing characters in addition to all the mixed case cases. It will live or die based on the developers who are fighting for it. This was planned to be a convenient method to use Bitcoins without dealing with unhandy public keys and addresses. This article must not be construed as investment advice. This variety of addresses demonstrates, again, that addresses are just a mean to accept a payment which is assigned to a certain public key. In case you forgot to specify it - please contact our support team, they will be glad to handle it. Once you have successfully bought Ethereum or Bitcoin on Coinbase, you are ready to move onto the next step. The construction for BC1 addresses guarantees that up to 4 character errors or 4 transpositions in an address are always detected. Every wallet software you use can easily create a P2PKH address, or, to be more precise: So who were the crackpot developers who wrote this?
You got your First payout Click on the badge to view your Board of Honor. They made a mistake. HedgeTrade Login. Fraudsters create fake wallet apps and list them on google play store, they usually mimic real cryptocurrency wallet apps. Some of the more notable examples include the likes of Dash , Litecoin , and Dogecoin. We are updating our wallets software on a regular basis. Please see Where is my ETH token deposit? Other than Bitcoin or Cryptonote, Ethereum does not transform the address to base58, so it is in hexadecimal 0-F. TotalCrypto does recommend you withdraw your coins off the exchange and store them in your Steemit wallet. Every wallet software you use can easily create a P2PKH address, or, to be more precise: Ask Question. Finance Markets Trading. Like base the bech32 character set also excludes some visually confusing characters in addition to all the mixed case cases.
They made a mistake. In that extremely unlikely event 1 in 4. The less the language lets best eth pool for single card mining microshare bitcoin mining do, the easier it is to analyze and prove properties of a contract. For example, Monero is based on the Cryptonote algorithm. In order to run code on Ethereum, you need to first deploy the contract the deployment is digital currencies will create new elite a2 terminator innosilicon a transactionwhich costs a small amount of Ether. It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. If you have the private key for an address, only you can sign a transaction with cryptocurrency token assigned to this address — while everybody who knows your address can verify the validity of your signature. Search for: We recommend using GDAX and saving yourself some fees. So if an address has at least one capital letter, it will be invalid, if you make a typing error. Joshua Kolden Joshua Kolden 3, 18
Like many things in cryptocurrencythe topic of addresses starts to get really intriguing when it comes to Ethereum. You might know it; it looks like this:. What is Locktime? Technology Trading. Unfortunately, the blockchain security model is more akin to the older model. A hard fork would be impractical—what do you do about all of the transactions that occur downstream? But despite all that, I still think Ethereum is going to win in the long run. This leads to much stronger security guarantees, so multi-sigs are a standard in wallet security. And there were how to solo mine ultracoin how to start bitcoin mining with awesome miner free edition to change the address system, so what we use today is not the final iteration. Criminals kidnapping important people and asking for their ransom in Bitcoin for the release of their victim. This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. Bitcoin ticker japan genesis coin ethereum support this one is for you. Locate your transaction by inserting your hash on the corresponding blockchain explorer website and check the status. In this exchange hack some hackers try to hack the full exchange servers. In case your deposit is not reflected on your account, please check out below all possible reasons for. They are fundamentally why Ethereum will win in the long run—or if they abandon Ethereum, their abandonment will be why it loses. They made a mistake. BIP introduced BC1x style addresses also called bech
Blockchain Education Technology. This is used in combination with phishing to get access to user accounts login details, for example, you get a fake twitter account impersonating the founder of Ethereum and that account tells you that if you deposit your ETH into an account, your ETH will be doubled. This attack is important. This article will shine some light on the subject and aims to clear up any confusion one might have about the complexity of this structure. Nope, all the cryptography was sound. The construction for BC1 addresses guarantees that up to 4 character errors or 4 transpositions in an address are always detected. They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. If you believe that social network users will agree that they should be paid for their contributions, then backing Steem might not be a bad idea. It will live or die based on the developers who are fighting for it. Your Binance account should be good to go. You can try Decentralized exchanges for more security. How do I buy Bitcoin?
Reddit Cryptocurrency News Politics. How do we grade questions? Check if the transaction is confirmed in blockchain Locate your transaction by inserting your hash on the corresponding blockchain explorer website and check the status. For this base function, it does not matter what you do with the public key, what cryptographic algorithm you apply to convert it to an address, and how the address looks. But when users make mistakes they don't generally produce random strings they tend to make typos where a small number of characters are replaced with alternatives which are visually similar, audibly similar, keyboard-position similar, or case variations. So, is it correct to think that if you accidentally issued an invalid recipient, shouldn't it be possible to doublespend it back to yourself and get that verified quicker, since it will be rejected by most miners? The safer approach here would be to whitelist specific methods that the user is allowed to call. Other than Bitcoin or Cryptonote, Ethereum does not transform the address to base58, so it is in hexadecimal 0-F. If you were connected to the network when you made the transaction, your coins are lost. Fundamentals of Tezos. What are the types of exchanges? Blockchain addresses are a vital component when it comes to blockchain technology and cryptocurrency as a whole.