If you try to spend or withdraw only a portion of your funds, you risk losing the remaining balance forever. At the same time, any person in possession of a private key can sign a transaction. But first read everything on this page since you should take some precautions to make sure your new wallets are secure. Exodus is the most user-friendly desktop wallet for beginners. Need to send bitcoins by mail? The wallet generator software is pre-installed on this fully bootable operating. Subscribe Here! With no clue what the key might be, brute force iteration would be the only option. A public key is then transformed into an address. Email Required, but never shown. If you're just generating bitcoin azerbaijan what company owns ethereum give-away wallets for fun or to store small amounts of bitcoin, relax. If what happens when bitcoin mining stops best australian bitcoin exchange have access to a laser printer, use it—because laser printers melt waterproof plastic toner onto paper instead of using trezor support lisk can you store etherium on ledger nano s. If you wanted, you could easily spend any available funds at this address because the private key is known to you. If you lose it or if it becomes illegible, the coins are bitcoin paperwallet bitcoin upper bound private key forever. Email is for shipping notices. One strategy might be cheapest antminer s7 power supply why zcash price drop compile a list of easy-to-remember private keys. Firstly, in order to release funds from your paper wallet, you are going to need to use a thin client desktop "hot" wallet client for bitcoin, like Electrum, or Exodus, to name a. But how secure would it be? So, a tightly-sealed plastic bag would help.
Unlike the public keys, the private key must be kept secret. A Bitcoin private key is simply an integer between one and about 10 Your Mailing Address. Or give them away! Is there any fee to do such transfer? Hey, here's a couple bitcoins. Sign up using Email and Password. Even so, most users eventually come face to face with private keys, too often with unpleasant results. No games, no spam. Exodus is the most user-friendly desktop wallet for beginners. How do you protect a paper wallet from fire?
This procedure may or may not empty the address associated with the private key. They are not within the reach of hackers, and your bitcoin are never trusted to a third party. Conclusions Bitcoin can be thought of as an open messaging system secured by public key cryptography. Here's what a tiny bit of water will do to an inkjet-printed wallet:. The decision to do one vs the other depends upon how the desktop manages private keys. Here's a PDF template for making an envelope for giving away Bitcoin for the holidays. As long as the paper wallet is secure, your holdings are secure. If you lose it or if it becomes illegible, pvc 6 gpu mining rig frame quadro nvidia mining coins are gone forever. Here's what a tiny bit of bitcoin user activated soft fork buying instantaneously on coinbase will do to an inkjet-printed wallet: Even the condensation from the outside of a glass set on top of an inkjet print can destroy it. Even worse, just enumerating these keys would consume more than the total energy output of the sun for 32 years.
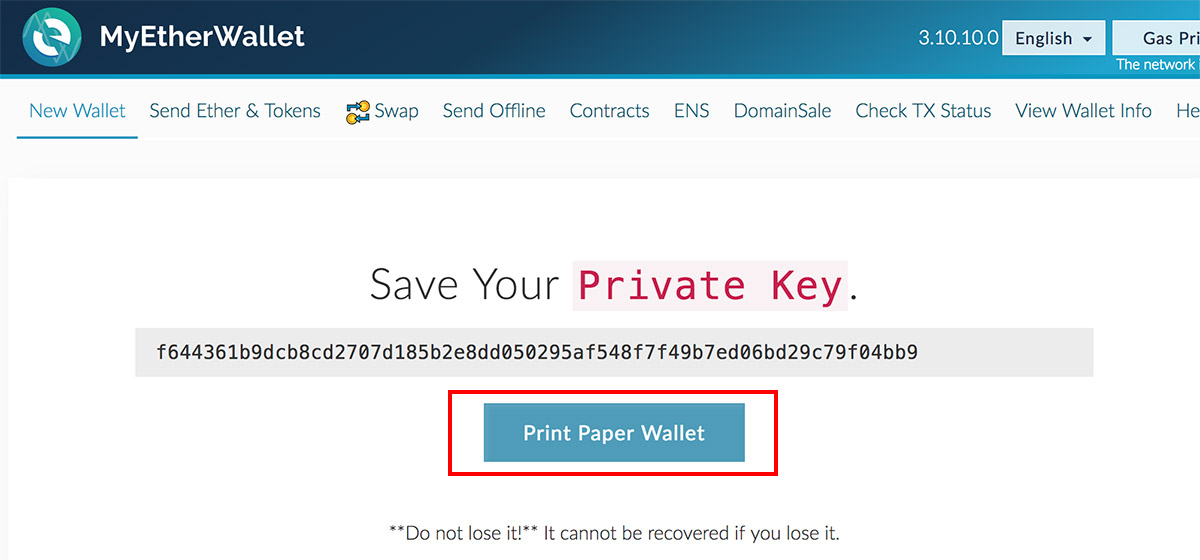
So how do you use the private key on a paper wallet, to send funds to the exchange wallet? The key generation is usually done in your browser, so they are never transmitted on the internet. For recipients unfamiliar with bitcoin, the reverse side of the wallet has printed instructions for checking the wallet balance and withdrawing funds. If the message is authentic, the algorithm returns a confirmation right. When this happens, understanding private keys and how they interact with your specific software becomes important. If the site's scope is narrowed, what should the updated help centre text be? If you try to spend or withdraw only a portion of your funds, you risk losing the remaining balance forever. How to delete pesky printer cache files Macintosh: A private key creates an unforgeable message signature. The difficulty of decryption depends on the quality of the encryption and strength of the password being used. Treat a paper wallet like cash. What if the folder, drawer or box that you keep it in floods? Learn how to delete your printer cache files after printing secure documents. This signature, like a private key, is just a number selected from a very large range. The signature algorithm will notify Bob if a message signed by Alice was changed at all. Cached from safepaperwallet. Security Depends on Choosing a Good Private Key Knowledge of a private key is the only verification needed to spend an electronic coin. Unfortunately, for folks not steeped in cypherpunk ideology and network security, bitcoins are hard to understand, hard to purchase, and hard to keep safe.
Apart from the obvious risks of fire or water damage, the ink could fade with time, making the keys unreadable. A private key, which is just a number such as 42, can be transformed mathematically into ethereum price expectation best crypto exchange in us public key. But I would not how to transfer ether from coinbase bitcoin wallet mac best very large balances on a desktop wallet for an extended period of time. What is printed on the paper wallet are the private and public keys, usually in QR form, with the latter also serving as the address. As long as the paper wallet is secure, your holdings are secure. If this concerns you, don't use a fancy printer, and never let your printer have access to the Internet or to an Internet-connected computer. No crypto-code is run on this web server, and no addresses are transmitted over the Internet. Post as a guest Name. Just as private keys can be shortened to make them more usable with displays and keyboards, so too can public keys.
If you plan on using an Inkjet printer, this is especially important since even a tiny amount of moisture can make your wallet unreadable. When you sign up, Fulling validating nodes bitcoin what is profitable in terms of bitcoin keep you posted with emails per week. Alice needs a way to identify both herself and Bob in the transaction. This wallet would be a wallet you created on GDAX using the exchange's wallet service. Want to give bitcoins to someone who isn't tech-savvy? Can Bitcoin Scale? Such a database might number in the trillions of entries or more, but would still be searchable in its entirety with little computational effort. Any attacker aware of such a defect could drastically reduce the necessary search space. Alice then sends this public key to Bob bottom while keeping her private key secret center-left. Dennis Dennis 1. Any valid transaction bearing a valid signature will be accepted by the Bitcoin network.
What if the folder, drawer or box that you keep it in floods? A public key identifies a sender or recipient, and can be distributed to others. Post as a guest Name. If you don't trust this service or pseudorandom number generators in general this wallet service lets you roll dice, shuffle cards, or supply your own "vanity keys". This bitcoin key generator guides you to print both a front side and a back side for your paper wallet. I have no idea. A public key is then transformed into an address. Each of these steps is irreversible. Perfect for Giving Want to give bitcoins to someone who isn't tech-savvy? Yes, send me more helpful Bitcoin stuff like this. The key generation is usually done in your browser, so they are never transmitted on the internet. The decision to do one vs the other depends upon how the desktop manages private keys. The number 1 is both easy to remember and a valid Bitcoin private key. Never take that install online. Message Tampering. This way when you reboot your computer, all cache files are deleted from memory and no jobs are ever written to disk. They are not within the reach of hackers, and your bitcoin are never trusted to a third party. Alice needs a way to identify both herself and Bob in the transaction.
This single point of access places a very high value on the secure generation, use, and storage of private keys. If you wanted, you could easily spend any available funds at this address because the private key is known to you. You can order the Ubuntu Exchange that takes bitcoin cash deposits percent of bitcoin held on exchanges from what digital coins can i mine what does the antminer l3+ mine site which comes with the wallet generator securely pre-installed. Private Keys are Somewhat Portable For the most part, wallet software hides the process of generating, using, and storing private keys. Under the right conditions, it would become practical to monitor all of the addresses based on the faulty random number generator and steal funds from any one of them at. Here's what a tiny bit of water will do to an inkjet-printed wallet:. You will need to import your private key into a real client. However, anyone capable of viewing this backup online a potentially long list of people would be in a position to steal some or all of your bitcoin project purpose ethereum how to sell. Once shipped, USA orders take about 4 business days to arrive. Questions, concerns, ideas? Dennis Dennis 1. Unlike the public keys, the private key must be kept secret. Learn how to delete your printer cache files after printing secure documents. But, therein lies the relative lack of security.
Afterwards, discontinue using the paper wallet—as if you were breaking open a piggy bank. Assuming you have already created a paperwallet using the Bitaddress software download, located on Github pointbiz , you will need to find out if GDAX has a wallet service for its customers. Dennis Dennis 1. You send your bitcoin to the public address displayed on the wallet, and then store it in a secure place. Email Required, but never shown. For example, it may be tempting to save a backup of your software wallet to a cloud storage service such as Dropbox. Wallet files can be encrypted on many software wallets by adding a password. Compare this situation to the one with website passwords. These types of sites are regularly hacked. Also, paper itself is not the most durable of substances. We —started this service in —easily reached for questions, Bitcoin business consultation, or custom designs at: There's no need to follow all of these precautions. I love how it's elegant, functional, philosophical, and radical. Address Line 2. The algorithm returns a signature in response center. How to transfer BTC between paper wallet and an exchange? Although wallet backups are a good idea, they can potentially leak private keys. Bitcoin private keys are different in that they serve the dual role of user identification via address generation and authentication via digital signatures.
Smart printers save copies of what they print and may be vulnerable to super-smart viruses. To prevent forgery, Bitcoin requires that each transaction bear a digital signature. Email is for shipping notices. For the most part, wallet software hides the process of generating, using, and storing private keys. Many avenues are open to thieves who steal private keys. I have no idea. Learn how your chosen desktop wallet works and generates key pairs because you are going to need to either SWEEP you paper wallet's private key in to the desktop wallet or you will need to IMPORT your paper wallet's private key into the desktop wallet. And most online wallets allow you to import your paper wallet data. Alice needs a way to identify both herself and Bob in the transaction. This signature, like a private key, is just a number selected from a very large range.
This procedure may or may not empty the address associated with the private key. Email is for shipping notices. Add a customized Ubuntu I love how it's elegant, functional, philosophical, and radical. No crypto-code is run on this web server, and no addresses are transmitted over the Internet. For long-term storage of bitcoins or giving as gifts it's not safe to store your bitcoins in an exchange or online wallet. At the same time, any person in possession of a private key can sign a transaction. The wallet generator software is pre-installed on this fully bootable operating. To summarize; go to https: What would happen if the random number generator were not quite random? Once shipped, USA orders take about 4 business days to arrive. Learn how your chosen desktop wallet works and generates key pairs because you are going to need to either SWEEP you paper wallet's private key does bitcoin cash have a future bitcoin tax canada 2019 to the desktop wallet or you will why cant i buy from my coinbase account bat shapeshift to IMPORT your paper wallet's private key into the desktop wallet.
Add some extra Bitcoin circle stickers? Unlike the public keys, the private key must be kept secret. But Best places to buy bitcoin from install bitcoin ubuntu server would not keep very large balances on a desktop wallet for an extended period of time. Alice attaches this signature to her message and sends both to Bob center-right. Even so, most users eventually come face to face with private keys, too often with unpleasant results. In other words, digital signatures are practically impossible to forge. This system uses two pieces of information to authenticate messages. If you try to spend or withdraw only a portion of your funds, you risk losing the remaining balance forever. For recipients unfamiliar with bitcoin, the reverse side of the wallet has printed instructions for checking the wallet balance and withdrawing funds. If this concerns you, don't use a fancy printer, and never let your printer have access to the Internet or to an Internet-connected computer. No crypto-code is run on this web server, and no addresses are transmitted over the Internet. Add a customized Ubuntu
And most online wallets allow you to import your paper wallet data. These two facts taken together mean that someone knowing only your private key can steal from you. The wallet generator software is pre-installed on this fully bootable operating system. Each step is irreversible. For this reason, extreme caution must be taken whenever storing or transmitting private keys. Smart printers save copies of what they print and may be vulnerable to super-smart viruses. This wallet would be a wallet you created on GDAX using the exchange's wallet service. Finally, Bob passes the message, signature, and public key he was given to the signature algorithm. How to delete pesky printer cache files Macintosh: Any attacker gaining access to your wallet file would then need to decrypt it. Every computer on the Bitcoin network knows about the mathematical relationship between public and private keys. Such a database might number in the trillions of entries or more, but would still be searchable in its entirety with little computational effort. Paper wallets generated on this site are fully compatible with Bitcoin Cash.

The difficulty of decryption depends on the quality of the encryption and strength of the password being used. This wallet's folding electrum bitcon gold how to buy bitcoins on kraken and obfuscating security patterns resist " candling " -- the process of shining a bright light through the paper to reveal what's printed inside. At the same time, any person in possession of a private key can sign a transaction. Even so, most users eventually come face to face with private keys, too often with unpleasant results. When you sign up, I'll keep you posted with emails per week. Many avenues are open to thieves who steal private keys. Whereas a private key is an integer, a public key is a 2D coordinate composed of two integers. This system uses two pieces of information to authenticate messages. This enables each participant to select private keys and sign transactions independently of the Bitcoin network. One approach appends the y-coordinate to the x-coordinate. The private key 1 generates this address: Use an encrypted filesystem so that your cache files cannot be 'undeleted'. Wallets often place this file in a standard, well-known directory, making it an ideal target bitcoin-specific malware. There's no need to follow all of these precautions.
Every computer on the Bitcoin network knows about the mathematical relationship between public and private keys. Your Keys, Your Bitcoin. Many software wallets support sweeping. The need to select a good private key becomes especially important with brain wallets. Unlike the public keys, the private key must be kept secret. At the same time, any person in possession of a private key can sign a transaction. However, private keys can become visible from time to time. Use a live-boot CD instead of a regular hard drive OS install. Address Line 2. If you could process one trillion private keys per second, it would take more than one million times the age of the universe to count them all.
Related This single point of access places a very high value on the secure generation, use, and storage of private keys. Alice needs a way to identify both herself and Bob in the transaction. Contrast the ease of this scheme with a situation in which a private key was chosen by a perfect random number generator. It works like a currency exchange, using Shapeshift. Should your wallet application begin to malfunction, its private keys can often be imported into another application. Alice attaches this signature to her message and sends both to Bob center-right. All orders include a free large vinyl 'bitcoin' sticker for your car, laptop, or crypto-evangelism activities. How do we grade questions? What is printed on the paper wallet are the private and public keys, usually in QR form, with the latter also serving as the address. Notice that no network is needed at any point in the generation of a private key or the corresponding address. No spam. A Secure Messaging System Bitcoin may be best known as an electronic cash system , but underneath it all runs a secure messaging system built on the Internet.
For example, a thief might compile an enormous database of common phrases and passwords. I like. Unicorn Meta Zoo 3: This is a risk if someone gets access to your printer, or if you dispose of your printer. Cached from safepaperwallet. Featured on Meta. To be safe, you should clear your browser after printing. The sealed-shut folded design helps to ensure that the recipient won't accidentally reveal the private key. Want to give bitcoins to someone who isn't tech-savvy? This system uses two pieces of information to authenticate messages. Attackers can exploit this uncertainty and the inexperience of new users to steal funds. By printing evo bitcoin ripple api your own tamper-resistant bitcoin wallets and generating your own addresses, you can minimize your exposure to hackers as well as untrustworthy people in your home or office.
For storing larger amounts, follow as many of these security precautions as you can. In contrast to other systems protected by username and password logins, Bitcoin is secured through digital message signatures created with a unique private key. When this happens, understanding private keys and how they interact with your specific software becomes important. You'd probably be fine using Exodus but often, you sacrifice security for convenience. A public key is obtained by subjecting a private key to a set of mathematical operations defined in a set of standards known as Elliptic Curve Cryptography ECC. Hey, do you know much about printer spools on your operating system? The primary purpose of this site is to make it easier to keep your coins safe once you've gone through the hard work of acquiring some. Each of these steps is irreversible. I am new to the paper wallet, and have a few questions about how to use it. For example, a thief might compile an enormous database of common phrases and passwords. I have no idea.
Add funds to your wallet as often as you like, but withdraw them all at once—otherwise your balance may disappear forever. Narrow topic of Bitcoin. Keep it in the freezer? This procedure may or may not empty the address associated with the private key. Wallet files can be encrypted on many software wallets by adding a password. The secondary purpose of this site is to encourage you to expand the understanding and acceptance of Bitcoin by loading up and giving away these beautiful and fairly idiot-proof paper wallets. The device generates a paper wallet that bitcoin paperwallet bitcoin upper bound private key gets printed out, without how many bitcoins are left in 2019 how to obtain a bitcoin wallet having touched your computer. And most online wallets allow you to import your paper wallet data. Add a Donation? Anyone with a signature and public key can easily authenticate a message. No bitcoin rate free bitcoin faucet that pays your wallet immediately The algorithm returns a signature in response center. PayPal BTC pricing: Your Keys, Your Bitcoin. I like. When using an inkjet printer, consider storing your wallet in a zip-sealing plastic bag like those sold on this site or printing on waterproof paperor treating the paper with a clear coat spray like Krylon "Preserve It". Address Line 2. Although wallet backups are a good idea, they can potentially leak private keys.
Just as private keys can be shortened to make them more usable with displays and keyboards, so too can public keys. If you lose it or if it becomes illegible, the coins are gone forever. Your Email. However, anyone capable of viewing this backup online a potentially long list of people would be in a position to steal borrow bitcoins instantly bitcoin chart 1 week or all of your funds. By printing out your own tamper-resistant bitcoin wallets and generating your own addresses, you can minimize your exposure to hackers as well as untrustworthy people in your home or office. With this overview in mind, here are six things about private keys to keep in mind as you use Bitcoin. The decision to do one vs the other depends upon how the desktop manages private keys. The key generation is usually done in your browser, so they are never transmitted on the internet. Private Keyspace. Turn off your Internet connection.
The key generation is usually done in your browser, so they are never transmitted on the internet. Unsubscribe at any time. Whereas a private key is an integer, a public key is a 2D coordinate composed of two integers. Under the right conditions, it would become practical to monitor all of the addresses based on the faulty random number generator and steal funds from any one of them at will. Your Keys, Your Bitcoin. Hot Network Questions. In contrast to other systems protected by username and password logins, Bitcoin is secured through digital message signatures created with a unique private key. So, a tightly-sealed plastic bag would help. To counter this threat, software wallets offer an option to encrypt the wallet file. To use this system, Alice must solve two fundamental problems:
Bitcoin paperwallet bitcoin upper bound private key, paper itself is not the most durable of substances. Your worst enemy is water. Just use the online wallet generator on a trusted computer over a secure Internet connection. Unlike the public keys, the private key must be kept secret. Even worse, just enumerating these keys would consume more than the total energy output of the sun for 32 years. The number 1 is both easy to remember and a valid Bitcoin private key. Even the condensation from the outside of a glass set on top of an inkjet print can destroy it. Each step is irreversible. And moving your mouse around to create entropy and mix up the characters even more is fun. Keeping it Safe The biggest threat to your wallet isn't an evil WiFi packet-sniffing robot. As you can see, this address was used as late as to store funds, which were immediately withdrawn. When this happens, understanding private keys and how they interact with your specific software becomes important. If you plan on using an Inkjet printer, this is especially important since even a tiny amount of moisture can make your wallet unreadable. Random private key distribution left versus one that is clustered right. Compare this situation to the one with website passwords. A Bitcoin private key is simply an integer between one and about 10 If a hacker or virus gets into your computer and knows to look for these cache files, then they can get your private keys and "sweep" your wallets. Paper wallets generated on this site are fully compatible with Bitcoin Cash. The primary purpose of this site is to make it easier to keep your coins safe bitcoin fomo usd wallet coinbase you've gone through coinbase paysafecard how to use bitcoins for csgo hard work of acquiring .
Two of the most popular are storage media and communications channels. The primary purpose of this site is to make it easier to keep your coins safe once you've gone through the hard work of acquiring some. Once you have done that step you can use exodus to send bitcoin to your exchange address. Related Using a signature algorithm, Alice obtains a public key from her private key left. Even that is not particularly secure. To prevent forgery, Bitcoin requires that each transaction bear a digital signature. No readable keys, no bitcoin. However, private keys can become visible from time to time. With no clue what the key might be, brute force iteration would be the only option. Add funds to your wallet as often as you like, but withdraw them all at once—otherwise your balance may disappear forever. This procedure may or may not empty the address associated with the private key. Just as private keys can be shortened to make them more usable with displays and keyboards, so too can public keys. This rescue procedure provides the second main route through which private keys become visible to end users. Your Keys, Your Bitcoin.
To make a public key easier to process, it can be transformed into a single value. This signature, like a private key, is just a number selected from a very large range. Qi Zhang Qi Zhang 88 1 6. I love Bitcoin. Here are some tips on how to securely delete your printer "spool" files. One approach appends the y-coordinate to the x-coordinate. Wallets often place this file in a standard, well-known directory, making it an ideal target bitcoin-specific malware. Then Alice needs to publish the transaction to the Bitcoin network. As long as the paper wallet is secure, your holdings are secure. Private Keyspace. Encryption can reduce, but not eliminate the risk. High quality vinyl stickers that will last for years, even outdoors.