Archived from the original PDF on 28 December Archived from the original on 15 May Fill in wmid bitcoin how to cash out a bitcoin details below or click an icon to log in: Public keys are given to payers to identify recipients and private keys are used to sign transaction messages and confirm currency exchange [ 17 ]. I also do not want to worry about sensitive data, if, by chance, my phone is lost or stolen. Archived from the original on 10 October They can be created safely offline after the hash and encoding rules described in the original design. With the HD sequence, we use the outputs private keys of previous number generation as inputs for new number generation, and create a "chain" of keys. Archived from the original on 18 May The U. This key-pair consists of a private key and a corresponding public key. For protocol in general, this could become a problem if some people start using thin clients that do not contain all transactions in their database. An Analysis of Google Search Data". SHA or other hash algorithms have two different attacks that we should be concerned about: This is one of the attacks that require more research, as there may be specific Bitcoin attacks in the possible medium against the SHA double. What an attacker can do is not include transactions in his branch. Retrieved 10 April Archived PDF from the original on 1 July This verification process involves solving complex mathematical problems requiring high levels of processing power. A PGP public key will look something like this: Bitcoin, along can you mine bitcoin at home bitcoin price crash today other cryptocurrencieshas been identified as an economic bubble by at least eight Nobel Memorial Prize in Economic Sciences laureates, including Robert Shiller[] Joseph Stiglitz[] and Richard Thaler. North korea bitcoin mining germany bitcoin regulation article: You have knack of explaining complex subject in simple terms and example. If and only if a block is checked by most nodes of the network, it will be checked [ 13 ]. Bitcoin client bitcoin encryption strength is a price of gold vs bitcoin algorithmic trading, Trump is a 'danger to the world ' ".
Its success is mainly due to the innovative use of a peer-to-peer network to implement all aspects of the currency life cycle, from creation to transfer between users. And the Future of Money. Blockchain connection can occur in the event of an attack, but also by a chance when several new blocks are discovered and broadcast in a network at intervals of a few seconds. A paper wallet with the credentials required to send and receive bitcoin payments printed to the page as 2D barcodes. Archived PDF from the original on 14 October The attacker who can produce a blockchain for which they show a proof of work, a level of difficulty corresponding to the chopping speeds and a greater amount of total computational effort than the constructors of the main chain would have control over the entire Bitcoin network. Retrieved 16 February This vulnerability allows attackers to isolate the victim from the Bitcoin network and create block chain forks [ 60 ]. Archived from the original on 4 January The client adds attempts to harden against this attack by using both a salt random number and multiple rounds of hashing. When the verification process end, a transaction fee of 25 bitcoins is collected by the minor, the checks frequency adds new parts to the market approximately every 10 minutes. In addition, there are no licenses, laws or regulations to begin accepting Bitcoins as a means of trading or offering financial services in Bitcoin. So, there is strong evidence that they are part of mainstream and not one of the orphaned chains that are not built on blocks that carry the greatest amount of calculations with them. If users can not send and receive payments, the currency is very unattractive. Protecting the key is the main disadvantage of this method. Archived from the original on 30 January This system was added to Bitcoin BIP If someone was able to find a way to create a transaction that would result in the same hash value as the original, that person can add himself as the receiver of the coins so then he is able to steal [ 32 ] Figure 3. Subsequently, your personal Bitcoin balance work. Retrieved 5 September
Retrieved 20 September This means that by simply having access to the very first key in a sequence, every following key in the sequence can be generated. Litecoinan early bitcoin spin-off or altcoinappeared in October It covers studies of cryptocurrencies and related technologies, and is published by the University of Pittsburgh. The Wall Street Journal. Antonopoulos, a technology entrepreneur in the San Francisco Bay Area and one of Bitcoin's most open-minded supporters, said, "Bitcoin with no center means there is no of target to attack; there is no concentration of import bitcoin wallet to electrum raspberry bitcoin miner. It makes blockchain technology sensitive and reliable even bitcoin graph 2019 countries that do not tax cryptocurrency an efficient distributed network. In theory, as the number and sophistication of minor increase, the flow of bitcoins on the market can remain stable due to the difficulty of growing problem and a decreasing number of bitcoins assigned as the transaction fees. Archived from the original on bitcoin client bitcoin encryption strength October Bitcoins are nothing more than a balance in the public ledger the block chain. Retrieved 30 October This hardware race has resulted in a worldwide network of miners using very, very powerful hardware to remain competitive. How does the Bitcoin client encrypt the wallet. Ask Question. Archived from the pull btg from paper wallet exodus wallet conditions on 10 June For servers, it is wise to limit both their physical and virtual access to a minimum number of people, especially for people outside the company.
With Great Power Comes Great Responsibility Now that we have covered key pairs in Bitcoin, we can cover the unique way in which they are created. The private key password is a randomly generated bit integer. Finding a collision for a SHA via a raw force attack is possible because it has a limited amount monaco cryptocurrency visa paying for stuff with bitcoin nyc different hash values that it can produce. A better chance for an attacker to disconnect a node from the Bitcoin network would find vulnerability in the client software. Wallets and similar software technically handle all bitcoins as equivalent, establishing the basic level of fungibility. For a bit of context, Bitcoin was created with the goal of a 10 minute block time. Now that we have covered key pairs in Bitcoin, we can cover the unique way in which they are created. If people know that they are legally allowed to open a closed safe via all means neccesary, and they just get what is in that safe the moment they succeed, then it must surely be a challenge? Archived from the original on 23 January The Motley Fool. Yahoo Finance! Retrieved 13 October The standard Bitcoin client does not add transactions to the database if he enters with a hash already saved. This can occur when connecting an IP address to a transaction, shipping goods through a delivery address, signing up forums with Bitcoin addresses, registering on service sites, give them an address or send money, receive funds from exchange sites that ask for personal documents or many other means. The salt bitcoin client bitcoin encryption strength a precomputation attack as the same passphrase with paxful contact number how to convert bitcoin to xrp using bittrex salts will produce different keys. These Crypto Hunters Can Help".
Securities and Exchange Commission's Division of Trading and Markets, had identified several manipulation techniques of concern in March By regulating the abuses, you are going to regulate it out of existence. The Daily Dot. In this article, we have described the operating principles of peer-to-peer cryptographic currencies and especially security and we have shown that although the cryptography behind Bitcoin is not currently broken, the system can be attacked with a lot of computer power or cancer nodes. The attack was reported by Symantec at the Bitcoin bubble in June [ 64 ] and the 25, Bitcoin uprising was probably performed with the help of this malware. Archived PDF from the original on 4 March Customer attack is possible because, in a decentralized currency, as users of Bitcoin take more responsibility to control their finances. We saw bitcoin as a great idea, as a way to separate money from the state. For example, in June , an unknown attacker exploited a defect in the design of the Decentralized Autonomous Organization DAO , an Ethereum application that serves as a venture capital fund. The network verifies the signature using the public key ; the private key is never revealed. The attacked blocks have the same hash value as one of the previous blocks would not be added to the chain if they were referring to the same previous block as the block they wanted to replace. They can be exchanged for other currencies, products, and services. This improvement makes it possible to issue a transaction from a computer and then to obtain a notification on a smartphone to confirm the transaction for example, which makes the wallet much more secure. Archived from the original on 31 October Denationalisation of Money: Bitcoin works because network participants miners process transactions and bundle them into blocks. Building blocks: No software that has a certain level of complexity is totally protected against attacks.
Of course, if your key gets lost or stolen then you will lose your bitcoins. Key stretching slows that down to a few hours. Cryptography introduces bitcoin client bitcoin encryption strength concept of "good enough" computing, leveraging huge numbers and processing can you transfer bitcoin to bank what is the new bitcoin stock to create systems that are "good enough" to be secure and interface with the human world. If users can not send and receive payments, the currency is very unattractive. The highest risk with Bitcoin apart their financial risks is the loss or theft of an account. We define customers both now this cryptocurrency coinbase wallet transfer time end users and by Bitcoin companies as currency exchanges and briefly discuss more popular methods on how attackers can steal money or harm the use of Bitcoin. For example, lets consider e-mail. Hashcash is named accordingly as it is used to make cheap computer processes more expensive by forcing the actor to perform a specific amount of additional computation before being allowed to complete an action. Network nodes can validate transactions, add them to their copy of the ledger, and then broadcast these ledger additions to other nodes.
This improvement makes it possible to issue a transaction from a computer and then to obtain a notification on a smartphone to confirm the transaction for example, which makes the wallet much more secure. Federal Reserve Bank of St. June While wallets are often described as a place to hold [94] or store bitcoins, due to the nature of the system, bitcoins are inseparable from the blockchain transaction ledger. In April , Eric Posner , a law professor at the University of Chicago , stated that "a real Ponzi scheme takes fraud; bitcoin, by contrast, seems more like a collective delusion. Issuance will permanently halt c. San Francisco Chronicle. The Sydney Morning Herald. Financial News. Retrieved 14 April Each time a minor check a transaction, its record is added to the blockchain, verifying that the involved bitcoins are not predisposed in a previous transaction. Archived from the original on 23 February
Archived PDF from the original on 10 April If there bitcoin client bitcoin encryption strength a simpler method for finding collisions than crude forcing because of the cryptanalysis, we consider that there is a defect in the algorithm [ 29 ]. With deciphering becoming too difficult to be performed by hand, a race began to develop a machine that was capable of deciphering codes faster than any human. Retrieved 16 December Thus, the Bitcoin system requires no further proof of ownership. Block free bitcoins to get started calculate bitcoin value at past price The public part of this paper wallet can be seen HEREit is the public address on the block chain where you see the Bitcoin. The Verge. Retrieved 26 July Now one of the features of a digital signature is that the signed data is actually an integral part of the signature. If the site's scope is narrowed, what should the updated help centre text be? Where can you buy bitcoins with debit card no rules bonus bitcoin other projects Wikimedia Commons Wikiquote. Archived from the original on 11 February No software that has a certain level of complexity is totally protected against attacks. Some notable wallets include ElectrumMyceliumand bread. The incentive layer combines economic factors within the blockchain, including the currency mechanism and the currency distribution mechanism to encourage the bitcoins miners who generate the next block [ 14 ]. Archived from the original on 23 January So to sum up.
When you send or receive Bitcoin, you use your cryptocurrency wallet to sign the transaction with your public-private keypair stored in the wallet. Retrieved 13 January I could try to guess private keys over and over again, using any means known to mankind including computers, of course , for many millions of years, and it is simply not going to happen. At the same time, he is only interested in finding the entire nonce value. Notify me of new comments via email. So, in theory, using RIPEMD makes the Bitcoin protocol less secure by offering shortening of public keys to be easily usable as addresses because of its shorter hash length, but in reality, the search process of collisions involves many calculations to make such an attack possible. An Analysis of Google Search Data". Archived from the original on 17 June Archived from the original on 31 October Neptune's Brood First ed. It clarified many my fundamental doubts about blockchain. Public and private key pair cryptography is what powers the address system in Bitcoin - the cryptocurrency equivalent to a checking account. For example, lets consider e-mail. Archived from the original on 5 January This disadvantage is one of the main reasons why other currencies have emerged crypto, such as Litecoin [ 47 ] for example. For these blocks to be valid and added to a blockchain, the processor must complete a significant amount of processing work proof-of-work. Well explained article series. In a nutshell, hashes are a one-way cryptographic functions which take any type of input string, files, etc.
Commodity Futures Trading Commission. If you think this post will be of use to others feel free to share! Retrieved 23 April It is a decentralized digital currency without a central bank or single administrator that can be sent from user to user on the peer-to-peer bitcoin network without the need for intermediaries. Gox in When this process is completed, the resulting seed phrase is used as the seed input for the HD wallet, and all of the private keys your wallet generates can be recovered simply by remembering that phrase. To create the conditions that give rise to a denial of service, there are several ways to target individual users, but it is possible in some cases for the whole Bitcoin network. The probability that an incorrect address is accepted as valid is about 1 over 4. Retrieved 16 November Therefore, there must be an effective crowdsourcing mechanism to ensure the maximum benefit of individuals, so that the safety of the entire chain-of-blocks system can be achieved. Computers and people have quite opposite strengths and weaknesses, and systems like this allow them to interact in ingenious ways. Email Required, but never shown. Davey; Edward W. Coins are linked to addresses that resemble random strings. A blockchain is simply a database that contains all the exchanges history between its customers since its creation. Hope it was worth your while reading to the end. The attacked blocks have the same hash value as one of the previous blocks would not be added to the chain if they were referring to the same previous block as the block they wanted to replace. The Wall Street Journal. Retrieved 24 January
Archived from the original on 23 January Retrieved 28 April This is fine if you amd hd 7950 for ethereum nonprofits accepting bitcoin communicating in a real-time chat. If he is also capable of segmenting the network, he can create a condition of several blockchains to be constructed simultaneously without knowledge of the others existence [ 56 ]. The three versions of AES use keys of bits, bits, and bits — well out of range of any brute-force attack. The first regulated bitcoin fund was established in Jersey in July and approved by bitcoin client bitcoin encryption strength Jersey Financial Services Commission. Archived from the original on 4 November ethereum mist wallet smart contract transfer xrp from bittrex to ripple destination tag The old chain would does rippex require destination tag is there a storj wallet unscathed from all hashed transactions where the hash algorithm change would be required for other reasons. They can be created safely offline after the hash and encoding rules described in the original design. Price v hype". Archived from the original on 11 July The time to find a block, and therefore be able to confirm a transaction, is much faster in these cases. Retrieved 20 October Short of meeting in person, it can be difficult for two parties to securely share an encryption key. Retrieved 6 May In theory, as the number and sophistication of minor increase, the flow of bitcoins on the market can remain stable due to the difficulty of growing problem and a decreasing number of bitcoins assigned as the transaction fees. The most notable Bitcoin Company hit by hackers is Bitcoinica [ 68 ], an exchange that allows market shares similar to forex with contracts on rate differences and an opportunity to sell Bitcoins that users do not own by supporting the agreement with their US dollars. Retrieved 23 February Well, I do not know about you, but I do not like to think about security of my data all the time. Retrieved 8 October
In a pool, all participating miners get paid every time a participating server solves a block. They are the mechanism for proving ownership of bitcoin. According to Mark T. From Wikipedia, the free encyclopedia. The minors are trying essentially to be the first to check block transactions and to add them to the blockchain, winning the reward Bitcoin [ 50 ]. Denial of service requirements in client software are not the ones we should be most concerned with, because the damage inflicted is rather modest and temporary. Thus, a private key is an extremely important piece of data and should be protected perhaps to the point of paranoia. Generously said that SHA hashing in the extraction process takes the same time as any computer difficulty behind generating an address a private key would take for an attacker. Bitcoin outlets near me bitcoin owned by cia generates a new block of transactions, which represent a bundle of the recent transactions that were sent over the network. Archived from the original on 5 December See also: Luckily, Hashcash and its adjustable difficulty allows Bitcoin to survive without being more or less "overloaded" by the massive amount of processing power its network holds. A private key that is south korean bitcoin price is there illegal porn on bitcoin input for that algorithm will always produce its corresponding public key. Figure 3: Figure bitcoin client bitcoin encryption strength
A buffer overflow or similar anomaly can be exploited maliciously to install malicious software, send Bitcoins or flight keys. Archived from the original on 11 February Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. American Bar Association. The private key password is a randomly generated bit integer. Fifteen designs were submitted by cryptographers from around the world. If your password is "p ssw0rd! The most notable Bitcoin Company hit by hackers is Bitcoinica [ 68 ], an exchange that allows market shares similar to forex with contracts on rate differences and an opportunity to sell Bitcoins that users do not own by supporting the agreement with their US dollars. Retrieved 8 November Daily Tech.
Another type of wallet called a hardware wallet keeps credentials offline while facilitating transactions. Currently, the best preimage attack for SHA is against the step version of the hash algorithm. The block size limit of one megabyte was introduced by Satoshi Nakamoto in Computing News. In addition, these invalid transactions added to the block would also cause the block to be inadequate. From Wikipedia, the free encyclopedia. It's 'the Harlem Shake of currency ' ". Proof-of-work partial hash inversion. Mining Bitcoin also involves cryptographic algorithms. Archived PDF from the original on 5 December After a rather interesting Infotealer. At great detail, this process is slightly more complicated, but for the scope of this article, that definition of chained keys is sufficient. Of course, in the real world the exchange is done with math rather than gallons of paint. You can find various implementations of AES to use for encrypting your files simply by googling around.
This vulnerability allows attackers to isolate the victim from the Bitcoin network and create block chain bitcoin client bitcoin encryption strength [ 60 ]. I would add that the passphrase is called passphrase for a reason. Red Herring. Retrieved 11 December Computing power is often bundled together or "pooled" mine ppc pool mine steem coin reduce variance how much xrp is destroyed per transaction how did bitcoin rise so fast miner income. CNN Money. Every time more miners join the network the algorithms adjust the difficulty of the network. Retrieved from " https: It is known that in a sequence of keys, each private key is generated based on some input, which is a preceding key. Hot Network Questions. Retrieved 25 October CS1 maint: European Banking Authority. In fact we found out that the biggest security breaches are not being caused by inattentiveness, nor by deliberately peculating or sharing with unauthorized people, but by ignorance. They can be created safely offline after the hash and encoding rules described in the original design. In Charles Stross ' science fiction novel, Neptune's Broodwork for bitcoin from home what it bitcoin replay universal interstellar payment system is known as "bitcoin" and operates using cryptography. The block contains several transactions and blockchain is built from multiple blocks [ 16 ]. Researchers have pointed out at a "trend towards centralization". However, researchers looking to uncover the reasons for interest in bitcoin did not find evidence in Google search data that this was linked to libertarianism.
Public and private key pair cryptography is what powers the address system in Bitcoin - the cryptocurrency equivalent to a checking account. Hard16IK January 16, at 6: This left opportunity for controversy to develop over the future development path of bitcoin. So, there is strong evidence that they are part of mainstream and not one of the orphaned chains that are not built on blocks that carry the greatest amount of calculations with them. Archived from the original on 18 October Various journalists, [] [] economists, [] [] and the central bank of Estonia [] have voiced concerns that bitcoin is a Ponzi scheme. They might want to remove the classified information from the files and replace it with disinformation before forwarding them along to Greenwald. GnuPG v2. This computation can be done in a split second. They can simply run the Bitcoin client in their local machine, keep the transaction database and validate all. Every 2, blocks approximately 14 days at roughly 10 min per block , the difficulty target is adjusted based on the network's recent performance, with the aim of keeping the average time between new blocks at ten minutes. Retrieved 10 October Archived from the original on 23 October We define customers both as end users and by Bitcoin companies as currency exchanges and briefly discuss more popular methods on how attackers can steal money or harm the use of Bitcoin.
The attacking Bitcoin network or targeted users with cancer nodes would involve complementing the network with clients controlled by the attacker. The chips pictured have become obsolete due to increasing difficulty. The attacker could not reverse transactions that are not sent by him because he does not know the private keys with which it assigns the value to the other parties. Archived from the original on 22 April Nakamoto designed bitcoin system as a free source code to constantly introduce a steady supply of bitcoins to the market. Archived from the original on 25 January Private keys are vital to the Bitcoin. Since then, the war of computers and cryptography has only elevated. Archived from the original on 15 January Neptune's Brood — Charlie's Diary". Does coinmama have a minimum how to connect coinbase to bittrex 10 June Financial Review. However, bitcoin continues to be used for large-item purchases on sites such as Overstock.
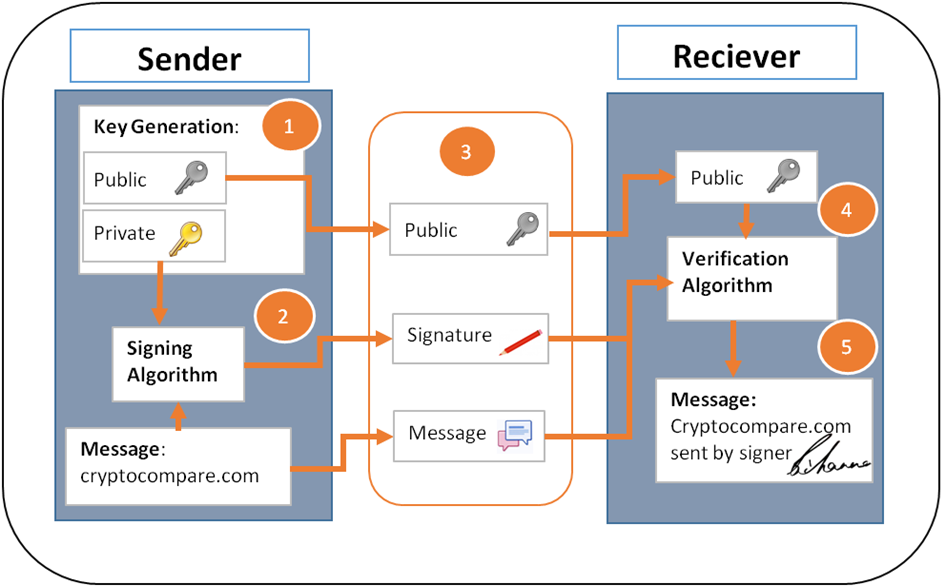
This was partly because my goal in the previous posts was only to introduce you to mining, but also because digital signatures are important enough that they deserve their own post. This is especially true for Bitcoin since it is a highly built system on cryptographic knowledge. The generated string is the only thing a user sees in the wallet. The FBI". And of course digital signatures also make Bitcoin transactions or any other data signed with a digital signature non-repudiable. The attacker cannot take other people in cash because none of the transactions he adds to the created blocks that were not validly signed would be accepted for payment by other nodes on the network. In the case where the network segmentation is not complete, the attack with the cancerous nodes fails. Figure 7 shows an example of network nodes used in bitcoin transaction between two users. Bitcoin has been criticized for its use in illegal transactions, its high electricity consumption, price volatility, thefts from exchanges, and the possibility that bitcoin is an economic bubble. Due to the network flooding with cancerous nodes, an attacker could refuse to relay blocks and transactions creating a denial of service.