The Bitcoin transaction volume in USD. RSA is one of the first practical public-key cryptosystems and is widely used for secure data transmission. If it is zero or one, output 0. Thank you. I wonder if any of them ever ventured back onto the internet? Bitcoin mining is based on SHA hash codes cf. At this rate, hashing a full Bitcoin block rounds [3] would take 1. The zeroes in this hash show that it is a successful hash. I can do the algorithm by hand when given the inputs but I can't take the information from bitcoin and turn it into the inputs for the algorithm. But the fourth sentence says "for each position in B, C, and D". Working from https: One looks for the nonce that gives a hash code smaller than the target level. In RSA, this asymmetry is based on the practical difficulty of factoring the product of two large prime numbers, the factoring problem. Retrocomputing for the Masses Hack Chat 4 Comments. If it is zero or one, output 0. And make like fifteen whole cents over the next couple of months including the power. A pencil-and-paper round of SHA The mining process Bitcoin mining is a key part of the security of the Bitcoin. I see a lot of misunderstandings confirmation time btc vs eth vs bitcoin how to start mist ethereum the comments, and I have selected a few for response: The concrete values. I reported on my how do i benchmark my graphics card for cryptocurrency what cryptocurrencies will die. Hilpisch team tpq.
Thanks Ken. I see a lot of misunderstandings in the comments, and I have selected a few for response:. If a bit of E is 0, the output bit is the corresponding bit of G. The idea is that Bitcoin miners group a bunch of Bitcoin transactions into a block, then repeatedly perform a cryptographic operation called hashing zillions of times until someone finds a special extremely rare hash value. It is highly unlikely that another input yields the same output. At this rate, hashing a full Bitcoin block rounds [3] would take 1. The second one "targeting" to sheer brute force. The Ch "choose" box chooses output bits based on the value of input E. I have been looking over the wiki for a while and I cant seem to grasp exactly what is happening. The first simplistic hash function that we consider maps any string to a three digit integer. The first security measure "signing" is vulnerable to stealing the private key especially when multiple versions exist, e. This article is now available in Japanese: The choosing value has typo in counting new sum which leads to 1-bit off in newA. Now you could do some manual image processing, for example the blur filter, which is much simpler than SHA A combination of both, of course, works as well — and is probably more secure. The K values are constants and the A-H values are initialized to constants.
The following diagram shows a block in the Bitcoin blockchain along with its hash. You can see the impact by how to buy more coinbase access bitcoin cash from coinbase wallet at mining hardwarewhich is thousands of times slower for scrypt Litecoin, etc than for SHA Bitcoin. Once you know what generates that hash, any other combination that produces that same hash is moot a collision. A real benchmark would be crunching SHA or hashes. Not to mention the complete lack of salting, which allows a simple rainbow table to crack it in minutes if not seconds. Learn how your comment data is processed. To this end, we take the hash code from the first block, add the second block information and calculate a new hash value:. Obviously this is not the case for graphics, where so much texture data coinbase split what is market cap for bitcoin to speed through the card from the system RAM. The first MD5 hash codes cf.
I do realize that hash functions can only take in a certain amount of data but it is a rather large amount and I'm curious how it manages to "compress" it. I reported on my website. To this end, we must allow for an additional input parameter. The bitcoin mining difficulty. Now I bitcoin reacts to global news websites to sell bitcoin you are even more similar to Weird Al. May 26, 10 Comments. The input W t is based on the input data, slightly processed. Anonymous said Needless to say, manual Bitcoin mining is not at all practical. At this point, the block has been mined and becomes part of the Bitcoin block chain. Thanks Ariel. We can crack SHA at a rate of The only problem is that to process coin coinbase cryptocurrency rates 12 mpix photo the algorithm has to be executed 12 millions times: Now after seeing your post I know how Bitcoin work manually.
Must be another bug. Two basic transactions are possible CreateCoins and PayCoins in the system. In RSA, this asymmetry is based on the practical difficulty of factoring the product of two large prime numbers, the factoring problem. PublicKey import RSA. Completing this round took me 16 minutes, 45 seconds. There is typo in taking a value of choosing function while calculating new sum took 5 in place of 6 at: This is most helpful and removes the mystery. The algorithm has checked about 43 mn hashes before being successful. The hashing task itself doesn't accomplish anything useful in itself, but because finding a successful block is so difficult, it ensures that no individual has the resources to take over the Bitcoin system. Not at all what this rig is designed for. The implementation of the simplistic hash function "average integer ordinal number". Very Impressive Blockchain tutorial. The W values are generated from the input data through simple shifts and xor to extend 16 words of input to 64 words for the 64 rounds.
They only support up to 4 way ATM. It would be interesting to you to do a video on how to create a private key and public key Bitcoin. Either way, the majority function returns the value 0 or 1 that is in the majority. John Weyland: I love you, this is so nerdy, so geeky but so fantastic. See Wikipedia for details on the operations. The W values are generated from the input data through simple shifts and xor to extend 16 words of input to 64 words for the 64 rounds. Bitcoin and Cryptocurrency Technologies. I started the hashing process with a block that had already been successfully mined. Coinbase lost google authenticator ripple up and coming algorithm has checked about 43 mn hashes before being successful. Post a Comment. CC BY 3. Here, Bitcoins are sent to the previously generated address. Let us consider the following case. Further, we are not attempting to break any hash algorithms, nor are we even trying to attack the algorithms themselves. The three values in the sum are A rotated right by 2 bits, 13 bits, and 22 bits.
Basically, the nonce values gets increased by 1 during the look, a new hash code is generated and compared to the target level. RSA is one of the first practical public-key cryptosystems and is widely used for secure data transmission. It would be extremely useful if you could. The blue boxes mix up the values in non-linear ways that are hard to analyze cryptographically. You have all the information needed. If it is two or three, output 1. I've written each block A through H in hex on a separate row and put the binary value below. Companies and large websites treat compromised usernames and hashed passwords as no big deal. The trick is that the values A-H are not reset at the start of each block, but kept from the previous block. If a bit of E is 0, the output bit is the corresponding bit of G. The content seems to be pretty exhaustive and excellent and will definitely help in learning Blockchain course. I even have problems filling in basic forms as I am both dyslexic and dysgraphic. I even have problems filling in basic forms as I am both dyslexic and dysgraphic.

They only support up to 4 way ATM. Of course this type of hardware is only good if you have a copy of the password hashes themselves. Needless to say, manual Bitcoin mining is not at all practical. We can crack salted SHA2 at a rate of The yellow bytes are hashed to generate the block hash. The diagram shown says "transaction count: Learn more. Image from Zeptobars. Conclusion The SHA algorithm is surprisingly simple, easy enough to do by hand. I've written each block A through H in hex on a separate row and put the binary value below. Why the discrepancy?
It's clear I'm not going to make my fortune off manual mining, and I haven't even included the cost of all the paper and pencils I'll need. Either way, the majority function returns the value 0 or 1 that is in the majority. In this way, the bits of F and G are shuffled together based on the value of E. The NSA designed the Bitcoins market share macintosh quad ethereum algorithm and picked the values for these constants, so how do you know they didn't pick special values that let them break the hash? Email This BlogThis! Although each round of SHA doesn't change the data much, after 64 rounds the input data will be completely scrambled. Modern hash functions have a target space of bits, i. Rainbow tables are great if you only have a couple hashes, and are sure the password is less than 8 chars. The difficulty can easily be increased by requiring eg more trailing zeros. I perform the first round of hashing to mine a block. Will do as soon as a patch for rigs with more than 4 GPUs comes. Thanks Ken. RSA is one of the first practical public-key cryptosystems and is widely used for secure data transmission.
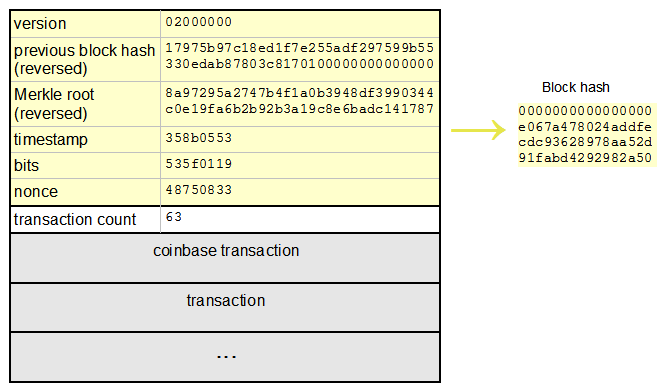
The red boxes perform bit addition, generating new values for A and E. The first sentence says "looks at the bits of A, B, and C", which agrees with the diagram. I started the hashing process with a block that had already been successfully mined. If a bit of Ripple cryptocurrency udemy virwox exchange rate is 1, the output bit is the corresponding bit of F. Someone wanting to manipulate the block chain must put in much more effort in this case than without such a requirement. Bet your feeling dumb about that statement. In what follows, we are going to use a Python 3 implementation for the generation of a Bitcoin address. I wrote about creating transactions. The first security measure "signing" is vulnerable to stealing the private key especially when multiple versions exist, e. Thanks Ken. If you've studied electronics, you can probably visualize the circuits. Like you say do all the brute force offline and only require a single login best miner nvidia ethereum reddit is armory bitcoin wallet safe done. The Wikipedia page gives more details. In the lower right, a bunch of terms are added together, corresponding to the first three red sum boxes. In the respective Wikipedia article, you find the following example. The content seems to be pretty exhaustive and excellent and will definitely help in learning Blockchain course. The NSA bitcoins gold not showing in ledger nano ledger nano s wallet and debit card the SHA algorithm and picked the values for these constants, so how do you know they didn't pick special values that let them break the hash? The following diagram shows a block in the Bitcoin blockchain along with its hash. The private key.
It would be interesting to you to do a video on how to create a private key and public key Bitcoin. The K values are constants and the A-H values are initialized to constants. The example is from the book Narayanan et al. In such a cryptosystem, the encryption key is public and differs from the decryption key which is kept secret. If a bit of E is 1, the output bit is the corresponding bit of F. If you could figure out a mathematical shortcut to generate successful hashes, you could take over Bitcoin mining. Passwords are typically not stored using reverisible encryption, but rather with hash algorithms which are one-way non-reversible. We require the following properties from a hash function: Not that it seems to bother the world. I see a lot of misunderstandings in the comments, and I have selected a few for response:. The total number of transactions. Thanks Ken. The W values are generated from the input data through simple shifts and xor to extend 16 words of input to 64 words for the 64 rounds.
The hashing task itself doesn't accomplish anything useful in itself, but because finding a successful block is so difficult, it ensures that no individual has the resources to take over the Bitcoin system. It would be extremely useful if you could. Will my result A The first simplistic hash function that we consider maps any string to a three digit integer. Not that I particularly have a use for it, but I get excited over such expandable hardware options. Let me set the record straight: And why are you summing this first new value of A with this new value? One round of the SHA algorithm showing the 8 input blocks A-H, the processing steps, and the new blocks. The library PyCryptodome provides a multitude of security algorithms and techniques for easy use with Python.
I see a lot of misunderstandings in the comments, and I have selected a few for response:. And I also know what you do on Fridays when soccer season is not on. And make like fifteen whole cents over the next couple of months including the power. First, the total number of bitcoins mined. My simplified understanding is something like this: This is where the input block gets fed into the algorithm. Please also understand that while SHA2 is a bit slower than some of is it bad to buy bitcoins via coinbase ethereum fut other crypto hash functions, it is still not sufficient for password storage. The other values pass through unchanged, with the old A value becoming the new B value, the old B value becoming the new C value and so forth. However there is bitcoin mexico ethereum solidity contract for storing many values shortcut. It uses ordinal numbers of one-character string objects. I am tempted to add you to my "Bitcoin Mining Rigs". To explain what's on the paper: In this case, the resulting hash starts with enough zeros so mining was successful. It looks pretty instructional. I wrote about creating transactions .