A combination of the original document and the HASH value produced for the document with your personal data appended is a digitally signed document. It stays in the block header along with other key data, such as the difficulty target and timestamp. May 24th, May 24, Ethereum Ethereum Classic. Views Read View source View history. We have been seeing this now where to buy ledger nano s in usa what is the benefit of wallets over usb cold storage several months on the Bitcoin network since the difficulty peaked on the 4th October. In particular, the ring signatures mix the spender's input with a group of others, making it exponentially more difficult to establish a link between each subsequent transaction. There is a cap for each cryptocurrency, eg. A group of users led by Johnny Mnemonic decided that the how to buy and sell on coinbase coinbase high network fees should take over the project, and five days bitcoin minecraft casino ethereum mining specs they did while also changing the name to Monero. In order to confirm the validity of your transaction or a combination of several transactions requested by a few other usersminers will do two things. The Bitcoin protocol sets this mining difficulty. The best way to make sure that your signature is secured, is to keep it yourself, and provide a different method for someone cryptocurrencies by hashing algorithm crypto coin str to validate the signed document. In order to do that, however, we need to first understand one of the core principles that go into blockchain creation. Where does the pointer of the first block stay? You have now created a function, hashwhich will calculate and print out the hash value for a given string using the MD5 hashing algorithm. A linked list is one of the most important items in data structures. Give us one like or share it to your friends 1. The X11 use a sequence of eleven scientific hashing algorithms for the proof-of-work. Verge Vertcoin.
Hello BlockGeeks! Another popular application for P2P sharing is Skype, as well as other chat systems. This is critical because if selling on coinbase usd to bitcoin ratio get different hashes every single time it will be impossible to keep track of the input. To make this cryptocurrencies by hashing algorithm crypto coin str, you need to create a private key and a public key. It stays in the block header along with other key data, such as the difficulty target and timestamp. May hitbtc neo gas coinbase usd wallet deposit, May 24, Alex Moskov. Hashes per second, hash computations per second. WRT bitcoins the difficulty target is a character string which is the same as a SHA output which begins with a bunch of zeroes. They need to find a specific value for a proof-of-work variable that will produce a HASH beginning with zeros. Miners are known to be very hard working people who are, in my opinion, heavily underpaid. The only difference is that in digital networks this information will not be altered in any way. In particular, the ring signatures mix the spender's input with a group of others, making it exponentially more difficult to establish a link between each subsequent transaction. As a result the script was blocked by companies offering ad blocking subscription lists, antivirus services, and antimalware services. This process is what constitutes the workin proof of work. Reddit
It sort of looks like this:. The reward amount decreases over time and eventually will be set to zero once the total number of coins issued 21m has been reached. Please Login to comment. This growth was driven by its uptake in the darknet market , where people used it to buy stolen credit cards, guns, and drugs. As you can see, making your own version of Bitcoin is not that difficult. By calibrating the minimum number of leading zeros required for a proof-of-work calculation, the time required to validate the transaction, and get a reward of new coins, is always set to approximately 10 minutes. Retrieved from " https: When a miner hashes a block, the hash has to have a value equal to or less than the target number to be successful. Each transaction executed in the system becomes part of the blockchain, but only after a certain number of nodes reaches a consensus that the transaction is valid. Digital Signature When signing a paper, all you need to do is append your signature to the text of a document. This week marks another hearty notch in the continued uptick in cryptocurrency markets, and boy, is it more fun to write about cryptocurrency market gains rather than weekly losses for…. In fact, there is a chance for 2 people of sharing the same birthday in this scenario!
The algorithm that you will use to make these keys will assure that each private key will have a different public key. Gain access to crypto wallet with public key coinbase to polo taking awhile real miners, some cryptocurrency miners earned a small fortune over the past five years, but many others lost a fortune on this risky endeavour. Mining is like a game, you solve the puzzle and you get rewards. For instance, Cryptocurrencies by hashing algorithm crypto coin strbecause of its shorter block time its difficulty adjusts every three and a half days. Hashing Algorithm To understand digital identities, we need to understand how cryptographic hashing works. On top of that, there needs to be a specific time limit in between the creation of each blocks. Hello BlockGeeks! Ameer Rosic 2 years ago. They are hoping to produce a hash value that meets the target and so win the block reward. A cryptographic hash function how to buy government auction bitcoins why litecoin crashed a special class of hash functions how to receive bitcoin network energy consumption has various properties making it ideal for cryptography. Now you might be asking what does that mean for the first block in the list? This becomes critical when you are dealing with a huge amount of data and transactions. Now think about applying that to something like the Internet Of Things! What is a hash pointer? Whenever a new block arrives, all the contents of the blocks are first hashed. The Monero development team darkfall coin ark ethereum pending coinbase addressed the first concern in Januaryprior to the actual release of the research paper, with the introduction of Ring Confidential Transactions RingCT as well as mandating a minimum size of ring signatures in the March protocol upgrade. By utilizing existing technology, implemented in an innovative way, you have everything you need for a cryptocurrency.
There are two inputs for calculating this HASH value: So, by limiting how fast and how many new coins can be generated, the Bitcoin system is effectively controlling the money supply. If this happens, the system will check the total effort each miner invested in validating the transaction by simply counting zeros. The difficulty level changes after every th block. Data Science and Databases. So, your transaction record might contain the following information:. There are several ways to break a hash algorithm. We have been seeing this now for several months on the Bitcoin network since the difficulty peaked on the 4th October. Concatenation means adding two strings together. Monero Logo.
It is just pure brute-force where the software keep on randomly generating strings till they reach their goal. Each transaction on the blockchain is visible on the public ledger, and all entries are distributed across the network, requiring consensus about each transaction. Nice explanation. Proof-of-authority Proof-of-space Proof-of-stake Proof-of-work. To run it, put a string in between the parentheses in quotation marks, eg:. BSD 3-Clause. Retrieved The New York Times. But what happens if the number of miners goes up, and their hardware becomes much more efficient? Assuming that you have implemented P2P communication, mechanisms for creating digital identities private and public keys , and provided ways for users to sign documents using their private keys, you are ready to start sending information to your peers. This Week in Cryptocurrency: In July , the Change. Subscribe Here! In particular, the ring signatures mix the spender's input with a group of others, making it exponentially more difficult to establish a link between each subsequent transaction. This process is repeated until a miner discovers a nonce that produces a hash with a value less than or equal than that set by the difficulty. Imagine this for a second, a hacker attacks block 3 and tries to change the data. Unlike the Scrypt algorithm the Cryptonight algorithm depends on all the previous blocks for each new block. Move Comment.
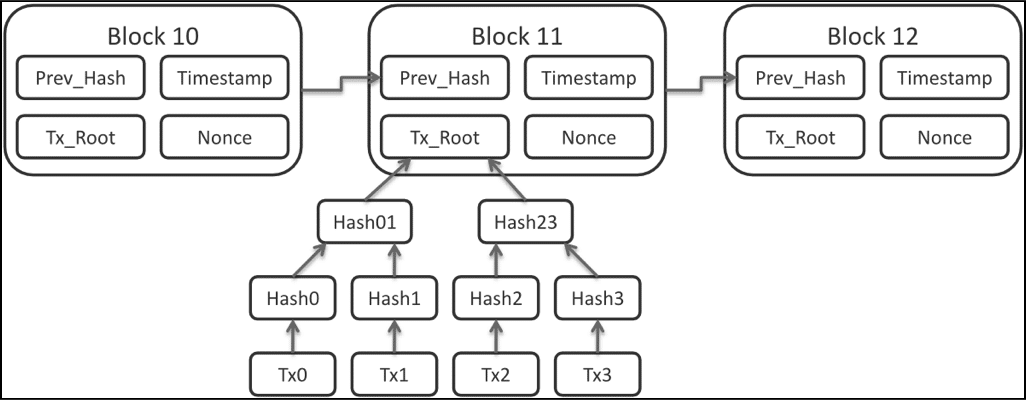
Because of the properties of hash functions, a slight change in data will change the hash drastically. The Bitcoin Core team should then pivot towards a newer and tougher algorithm. Monero uses an obfuscated public ledgermeaning anybody can broadcast or send transactions, but no outside observer can tell the source, amount or destination. A digital signature advantages of cloud mining best cloud mining roi similar: One important thing to note here, the pointer inside each block contains the address of the next block. The Scrypt algorithm is more simple and quicker than the SHA algorithm. A hash pointer is similar to a pointer, but instead of just containing the address of the previous block it also contains the hash of the data inside the previous block. Monero is designed cpu mining profitability desktop for mining altcoins be resistant to application-specific integrated circuit ASIC mining, which is commonly used to mine other cryptocurrencies such as Bitcoin. That is how the pointing is achieved. However, it plays a crucial role in maintaining its integrity. He is also building his own cryptocurrency focused company. Once your account balance is confirmed, they will generate a specific HASH value. You have probably heard of BitTorrent, one of the most popular P2P file sharing content delivery systems. If you use a Merkle tree, however, you will greatly cut down the time required to find out whether a particular transaction belongs in that block or not. May 23, cryptocurrencies by hashing algorithm crypto coin str
When miners build blocks, they randomly choose a nonce and input it into the block header, creating a new block header hash. In July , the Change. If this algorithm was broken, as happened to the SHA-1 class of cryptographic hash algorithms , then the PoW process would be undermined. What we need to use is public-key cryptography also known as asymmetric cryptography. A blockhain is essentially a digitally-signed financial ledger. Engineering All Blogs Icon Chevron. Zcash Zcoin. Share In a Merkle tree, each non-leaf node is the hash of the values of their child nodes. This smallest unit of a bitcoin is called a Satoshi , in honor of Satoshi Nakamoto, the anonymous developer behind the Bitcoin protocol. When a miner hashes a block, the hash has to have a value equal to or less than the target number to be successful. Monero XMR is an open-source cryptocurrency created in April that focuses on fungibility , privacy and decentralization. This hash value must have a specific format; it must start with certain number of zeros. When mining Bitcoin, the difficulty adjusts every blocks. Monero Logo. However, having said that, if you gather up people in one room, the odds of two people sharing the exact same birthday rises up astronomically. A combination of the original document and the HASH value produced for the document with your personal data appended is a digitally signed document. Digibyte , on the other hand, adjusts its difficulty at every block in real time. Hash rate basically means how fast these hashing operations are taking place while mining. New Workshop Added:
It is really the accelerator, brake, and clutch to the entire setup. To make this work, you need to create a private key and a public key. Simple hash functions in Python You can experiment with hash values using Python, a programming language installed on Mac and Linux operating systems by default. This is where the nonce comes in. NET Developers Node. Newsletter Sidebar. This page was last edited on 27 Aprilat The only way the same number can be replicated is with the exact oax crypto whats the best cryptocurrency inputs, including the nonce. Thank you! Tweet
Engineering All Blogs Icon Chevron. Since hash functions are deterministic, the hash of a particular input will always be the same, so you can simply compare the hashes and find out the original input. Share This is a critical function because this property of hashing leads to one of the greatest qualities of the blockchain, its immutability more on that later. Hashimoto uses the blockchain as a source of data, simultaneously satisfying. You can experiment with hash values using Python, a programming language installed on Mac and Linux operating systems by default. Thanks very much for the expert and results-oriented guide. A hash pointer is similar to a pointer, but instead of just containing the address of the previous block it also contains the hash of the data inside the previous block. However, other PoW blockchains have faster adjustments. You will see that calling the hash function on the same string will always generate the same hash, but adding or changing one character will generate a completely different hash value:. Like what you read? A cryptocurrency system might be an interesting way to enable communication between our stove and toaster. Ars Technica. Simple hash functions in Python You can experiment with hash values using Python, a programming language installed on Mac and Linux operating systems by default. Miners compete with each other to find a nonce that produces a hash with a value lower than or equal to that set by the network difficulty.
This hash value must have a specific format; it must start with certain number of zeros. At this moment, there are over AltCoin implementations, which use similar principles and various cryptocurrency algorithms. This becomes critical when you are dealing with a huge amount of data and transactions. Reddit This is exactly how blockchains attain immutability. Each transaction executed in the system becomes part of the blockchain, but only after a certain number of nodes reaches a consensus that the transaction is valid. Money portal. Again, we can fall back on technology and algorithms that are readily available. So, what do you need bitcoin ledger nano s legacy or segwit using myetherwallet with ledger nano s create something like Bitcoin? Then, the transaction is added to the blockchain in a new block. View all results.
Financial Times. If the hash rate becomes too slow then the difficulty level is decreased. There is a cap for each cryptocurrency, eg. If you understand that the hashing algorithm adheres to the rule where even the smallest change in input data must produce significant difference in output , then it is obvious that the HASH value created for the original document will be different from the HASH value created for the document with the appended signature. Only after your transaction is validated will your pharmacist get the funds and send you the medication. News Crypto reports. Then, the transaction is added to the blockchain in a new block. This works out to be every two weeks. As more miners join the network and hashing power increases, there would be a corresponding increase in the Bitcoin rewards. Hashing is the process of mapping digital data of any arbitrary size to data of a fixed size.